Phone Security and Surveillance | Renegade Cut
Nobody goes anywhere without their phone. Our phones are our address books, computers, watches, and calculators – but there is one other thing, one other feature of our phones that we try not to think about. Because if we think about it too much, we'll never stop thinking about it. Our phones are also tracking devices. Even if we turn off the Wifi, turn off mobile data, and stop using Google Maps, there are ways for our phones to be tracked and monitored. Through a combination of cell towers, Wifi, mobile data, apps, and other electronic methods, our phones can easily be tracked, and since we always bring our phones with us when we leave the home, we ourselves can also be tracked. As explained in Security and Counter-Surveillance, “Cell phones, because they operate through satellite and transmission tower networks, can be used to track a person’s movements and location. Cell phones can also be made into active listening devices, even when not in use.
Many also have built-in digital cameras and video capability. The proliferation of cell phones and their capabilities greatly expands the potential for surveillance...” We have given up privacy for convenience. We have given up our personal space and security
for devices that have made addicts of us. It's a remarkable addiction because contemporary society has made owning a smart phone so necessary that the addiction becomes mandatory. We can always turn them off, but now that everything is set up to be accessed by smart phone, permanently turning off our phones would be the same as permanently cutting ourselves off from the world.
We are being tracked at all times, but we also can't stop ourselves from this tracking, this loss of privacy, any more than we can simply decide to live in the woods or stay off the grid completely. Such an option technically exists but is not feasible or practical for comfortable living. Some people don't care about this and have simply accepted this as the new normal of the 21st century, but other people have more cause to be concerned about their privacy – namely activists, journalists, and others who might be doing important work that is nonetheless frowned upon by the state. Some people, understandably, feel the need to take greater precautions.
When Black Lives Matter protesters took to the streets, the United States Department of Justice contacted the US Marshals and DEA to provide support to local law enforcement. The DOJ saw this as an opportunity to collect data from activists under the guise of public safety. As explained by Kim Zetter of The Intercept, “...it’s likely that the two agencies were
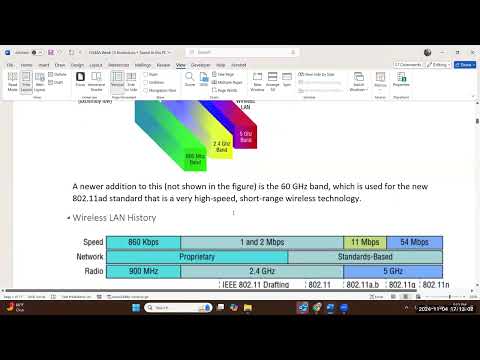
being asked to assist police for a particular reason. Both the DEA and the Marshals possess airplanes outfitted with so-called stingrays or dirtboxes: powerful technologies capable of tracking mobile phones or, depending on how they’re configured, collecting data and communications from mobile phones in bulk. Stingrays have been used on the ground and in the air by law enforcement for years but are highly controversial because they don’t just collect data from targeted phones; they collect data from any phone in the vicinity of a device. That data can be used to identify people — protesters, for example — and track their movements during and after demonstrations, as well as to identify others who associate with them. They also can inject spying software onto specific phones or direct the browser of a phone to a website where malware can be loaded onto it ...” Smart phones generally have a location service feature that uses signals received from GPS, Global Positioning System, or GLONASS, Global Navigation Satellite System. GPS is operated by the United States Department
of Defense, and GLONASS is operated by Roscomos, the Russian Space program. I'm sorry, but our smart phones really are subject to tracking by world superpowers, and their tracking is highly accurate. We lost the rights to our private lives a long time ago. Remember when the United States Congress passed the PATRIOT Act and said it was just about catching Osama bin Laden, and then it was reauthorized over and over again until everyone kinda got used to it? Well, now it's the new normal, and 20 years ago feels like a million years ago. Thanks a lot, everyone who got caught up in post-9/11 fear-mongering and propaganda. How close can the federal government pinpoint our location? Well, remember those cell towers? The greater the amount of towers, the more accurately a smart phone can be tracked. In urban areas,
there are a lot of cell towers whereas in the suburbs or especially in rural areas, there are fewer cell towers. When a phone enters the range of a cell tower, the network operators have some raw data because they know from which sector the phone arrived. When the distance is measured by multiple towers, they can effectively triangulate that phone's position in a process called uplink multilateration. 5G networks can triangulate your position within a few meters – basically right on top of you. Remember back in 2013 when leaked documents proved that the NSA was spying on millions of Americans without their knowledge? The spy program continues to this day. This isn't like the movies where the
bad guy is found out, and everything goes back to normal. Instead, the bad guy was found out, but since the bad guy is the state, the bad guy just kept doing roughly the same thing. As explained by Ellen Nakashima of The Washington Post, “An extensive surveillance program first revealed by former National Security Agency contractor Edward Snowden in 2013 continues to operate with no judicial and limited congressional oversight despite its potential to capture Americans’ communications … According to documents leaked by Snowden, the program has existed for more than a decade.” The data in our phones is of particular interest to the state. Our computers are
always in our home, but our phones come with us, and our phones contain an abundance of communication. Phone calls, text messages, and so forth. So, what can we do? Simply abandon our phones? Again, that does not seem entirely practical. We can be a little safer, though. We can adopt practices that limit our exposure, that limit our ability to be tracked at a moment's notice. There is no foolproof plan, but that doesn't mean accepting this loss of privacy altogether.
Let's go through some practical advice from experts and see what we can do. Malware is not just software from sketchy websites looking for your credit card information. It's also utilized by the state to dig deeper into your smart phone, to spy on journalists, to sabotage activists, and really to do whatever the state deems necessary. Mexico, India, Saudi Arabia and other nations have used Pegasus software to this end. Some nations like Italy,
Syria and Kazakhstan have used spyware called Hermit. Greece and Madagascar are using software called Predator. The list goes on and on. Spying on citizens has become big business. Much of this malicious software is the “no-click” variety, meaning we don't have to be tricked into clicking on some dodgy link to have it lodged into our devices. One method is abusing certificates to sideload itself from outside of the app store. This level of spyware is not something easily avoided by a simple antivirus app.
The United States, for examples, spends millions of dollars on their malware, and it's sophisticated enough that common, free anti-malware apps probably won't cut it. One bit of good news is that while this malicious software is powerful, it's also subject to the ever-changing world of internet software. Malware is often attuned to particular operating systems, and when the OS updates, the state must update their malware as well. If we update our OS frequently, we lessen our chances of being infected by state malware.
The Pegasus software, for example, has some weaknesses in this area. The infection chain has no “persistence” which means a normal reboot helps clean the device. The problem is most people don't reboot their mobile devices too often. Start making a habit of that. Reboot daily. Multiple times daily. It will force Pegasus to find your device again and try to re-infect it. Some apps like iMessage and Facetime on iOS and default apps on Android are commonly exploited because they are always on the devices. Disable default devices and replace them with more secure and less common apps instead. Speaking of which...
[Apps] [Orange and Blue] Some applications share more of your information than others. Some have access to your location, and that location can potentially be shared with the federal government, law enforcement agencies, private corporations and a number of other entities that you did not consent to share that information. As explained in the book Mobile Security and Privacy, “Apps such as Facebook, Foursquare, Swarm, Tinder, Twitter, Uber, and similar hold and share information about where you are exactly at what moment, not to mention a history of where you were. … One of the greater issues for privacy relates to continuing consumer trust in the digital economy. In the span of a few short years, social networking on the Internet has become the platform for communication among many mobile device users using apps like Twitter, Instagram, Facebook, or WhatsApp. Just because people are much more public in
the nature and extent of information they share online does not mean privacy is dead.” What apps and operating systems should you download? Apple IOS and Android's OS are well-known enough to be abused, but there are other operating systems that could offer better security. Android has a public source code, and those with security in mind have created alternate operating systems from it, such as LineageOS, GrapheneOS, and CalyxOS.
Some people believe that iOS is the most secure operating system available because Apple only releases its source code privately, but if your concern is state-sponsored malware, simply having an iPhone is not going to help. You think these huge corporations that supply governments with spy software don't have access to the iOS source code? Another downside of the IOS is that while there may be fewer vulnerabilities than vanilla Android OS, that also means that vulnerabilities do not get flagged as quickly. To further mask our presence, we can always use a combination of a VPN and Tor browser, which masks our footprint through multiple layers of encryption. As explained by Costin Raiu, “Some exploits are delivered through GSM operator MitM attacks, when browsing HTTP sites or by DNS hijack. Using a VPN to mask the traffic makes it difficult for your GSM
operator to target you directly over the Internet. It also complicates the targeting process if the attackers have control over your data stream, such as while in roaming.” By the way, do not rely on a free VPN. They are usually garbage. Tor browser is free, but it is not garbage. It is essential.
Turn on Encryption in your phone security settings, but for added security, use an encryption app like ZenCrypt, Crypt4All, or iDrive. Don't use your phone's SMS messenger. Use an encrypted messenger like Signal, Telegram, or Wire. Don't use Twitter or facebook direct messenger for anything you wouldn't want
the government because they absolutely will get access to it if they want to. Delete Google Maps from your phone and download an alternative like NavMii or OpenStreetMap. What about email? I remember when email blew up in the 90's and effectively replaced snail mail by the turn of the century. Email had been around for a long time, but not many people were really on the internet until the second half of the 90's. It felt more secure, less physical than envelopes that leave a literal paper trail. But here we are, it's 2023, and email is not secure at all. For email, do not use Gmail. Again, don't trust Google. Use
a more secure email and encrypted email service, or just bounce from email altogether and message through one of the aforementioned encrypted message apps. Never use an email account provided by your internet service provider, and never use your work email to discuss anything you don't want someone to see. Your boss will sell you out at the slightest hint of trouble. As explained in the book The Art of Invisibility by Kevin D. Mitnick “If you’re like me, one of the first things you do in the morning is check your e-mail. And, if you’re like me, you also wonder who else has read your e-mail. That’s not a paranoid concern. If you use a Web-based e-mail service such as Gmail or Outlook 365, the answer is kind of obvious and frightening.
Even if you delete an e-mail the moment you read it on your computer or mobile phone, that doesn’t necessarily erase the content. There’s still a copy of it somewhere. Web mail is cloud-based, so in order to be able to access it from any device anywhere, at any time, there have to be redundant copies. If you use Gmail, for example, a copy of every e-mail sent and received through your Gmail account is retained on various servers worldwide at Google. This is also true if you use e-mail systems provided by Yahoo, Apple, AT&T, Comcast, Microsoft, or even your workplace. Any e-mails you send can also be inspected, at any time, by the hosting company. Allegedly this is to filter out malware, but the reality is that
third parties can and do access our e-mails for other, more sinister and self-serving, reasons.” The federal government contacts big corporations and asks them for access to your accounts all the time. You think AT&T has your back? You think Comcast is run by activists? Always put several layers of security between yourself and a major corporation if you plan on staying safe from the NSA, FBI, CIA and other three-letter government goon squads. Imagine a gang sneaking on to your driveway or apartment building and rifling through your mail box. That's what the state is doing all the time – in your email inbox. So, what else can we do? Get yourself a Faraday Bag to protect your phone from receiving signals. A faraday bag is a shield
for your phone. It blocks electromagnetic fields. If you're worried that you're being tracked and you don't want to wrap your phone in aluminum foil all the time, a Faraday Bag is what you want. Be sure to get one with good online reviews or you're just buying an expensive purse. Some people mistakenly believe that removing the SIM card from the phone will prevent the phone from being tracked, but that is not true. Removing your SIM does not safeguard your phone from tracking. Here is why. When a phone connects to a cellular network,
they send a unique identification called the International Mobile Equipment Identity and subscriber identity called the International Mobile Subscriber Identity. The latter is generally stored on a physical SIM card or Subscriber Identity Module. However, a phone can operate without a valid SIM card or IMSI. These just authenticate the device to the carrier. That's why a phone can typically make emergency calls without a SIM card. In other words, a phone is still active and still trackable without that card. In fact,
switching multiple SIM cards in one device or one SIM card in multiple devices can create a trackable link between device ID and the subscriber ID. Lock your smart phone with a password. I'm not a lawyer, but according to lawyers, the current law is that a police officer can force you to unlock your phone with facial recognition, but the officer cannot force you to give up your password. So, if you think locking your phone with facial recognition is safer, that's not necessarily true, at least in this situation. Don't use a fingerprint lock unless you like the idea of your fingerprints being stored in your phone. Also, delete old data from your phone as much as possible. Some people also mistakenly believe that using an old phone with 2G or lower instead of a smart phone is more secure, but that is not exactly true.
According to Hakan Geiger, author of author of Mobile Phone Security for Activists and Agitators, “Because a phone without GPS or location service can still be geolocated, simple phones do not offer significant protection from location tracking. Feature phones typically lack widely available text or voice chat apps, and by definition basic phones have no such capabilities. This means that only unencrypted SMS and telephone calls are available, and these are susceptible to interception in more ways than if they had client-server or end-to-end encryption.
Basic phones ... may only have 2G capabilities which means that calls and SMS are trivially interceptable with only about €25 worth of consumer-grade equipment. Further, many of these devices may have hidden internet capabilities that send telemetry data back to manufacturers without users being aware.”
Do not pay for a burner phone with a credit card. That would defeat the purpose. Go to a convenience store or retailer, and pay with cash. Don't tie your burner phone to anything you do on your smart phone. There are far more secure smart phones out there, designed from the ground up for cyber security, but the prices are pretty steep. Hard to recommend for the average person, but something from Sirin Labs or Bittium might be worth it if you have serious security concerns. Even if you do all of this and more, your privacy and safety are not guaranteed. Nothing will completely prevent your phone from being monitored, but there are methods to potentially reduce that possibility. Use them. Use all of them, stay updated on new
technology, both to utilize and to avoid. Our private lives have been bought by corporations, and our safety is maintained by the state, and they will take it away if you prove yourself to be an agitator, or even if you're not. If your response to this is “I don't have anything to hide!”, that is the attitude that put us all in this situation in the first place. Be careful out there.
2023-04-30 19:48