How to Spot Any Spoofed & Fake Email (Ultimate Guide)
If you've ever received an email that claims to be from some company but it seems suspicious, this video is for you. There are plenty of ways for scammers to spoof email addresses, but here I'll show you how to tell if one is legit, using email authentication methods most of the big websites use at least, which are the ones most targeted by scammers. I'll mostly be using Gmail for the examples here because it has the most transparent information to see, but if you use other programs I'll show you some work arounds for those too. So yes, this is about to be a 20+ minute video just about how to tell if an email is fake, and we are going down the rabbit hole so buckle up.
There's more to it than you think. And remember you can always just throw the video on a faster speed if you want. Let me be clear though, this video is specifically and ONLY going to focus on how to tell if an email is really from the website it says it's from, NOT whether the email itself is safe or a scam. It's of course a critical part of identifying scams, but if a hacker uses their own domain to send out scams, obviously the tests will show the sending domain as genuine, but the sender is still a scammer! For example, at one part later in the video I'm going to show how to view some email checks Gmail has for verifying the sender, but if you look at them and say "oh, wow they all passed.
I guess this email from Hacker@StealYourMoney.scam must be completely safe because the Google said so..." well you completeley missed the very limited purpose of them. I'll try and keep the technical jargon to a minimum and just show you exactly what to look for, but I WILL need to explain what some of these things mean, because it's important to know WHY you're looking at these clues. Unfortunately scammers are smart, so everything I mention will take a bit of critical thinking along with it.
So just try to bear with me. And Also make sure you pay attention to ALL the steps, don't stop half way through, because then you'll think you're safe, but each next step will reveal scam techniques that were NOT caught in the previous. So step 1 is going to be a bunch of different ways to check if the 'from' domain in an email is even correct.
First with some obvious examples, then with some that are extremely clever. Let's say there's en email with a subject line and content that suggests it's from some company. No matter how legit it looks, the first thing to check is the 'from' address. Now I know this we're starting out with the really obvious stuff, but remember these CAN be spoofed, however if it's NOT spoofed, it is indeed the most obvious sign of a fake email. As an example from my spam box, this email says Fidelity Investments, but when you look, it's actually a Gmail address someone made with fidelity in the name. This is why you check this first, because now this case is so obviously a scam that no further investigation is needed.
So always make sure the 'from' address domain is EXACTLY what you would expect. Many scam emails don't even try to spoof domains, because unless done right, it's more likely to be caught in a spam filter. Also keep in mind when I say 'spoof', I mean they manipulate the email address so it actually shows a legit domain even though it wasn't sent from there, which is different than what we're seeing here, which is where they use a similar looking one, but we'll cover that later. Technically this could also be called spoofing but for the purpose of this video just know that distinction I'm going to make. In general, here are some things to look for. They might use a free email service like Gmail, Hotmail, Outlook, or other obscurer services you don't recognize as free email services.
What you do need to really watch out for though, are domains they bought that are chosen to look similar to the real domain. For example, if they are trying to impersonate Paypal.com, they might register the domain "Paypal-Mail-Server.com", which some people might just assume is real. This is why I said make sure the domain is EXACTLY what you expect, and not some other similar domain. Also be careful if they use subdomains. Maybe it says "Paypal.example.com", or "Paypal.com.[a bunch of random stuff].example.com".
Where example.com is the actual domain, not the stuff before it. Nothing before the final part means anything, so always look at the root domain only. Oh and also be sure to check they didn't use letters with umlauts above them or something, or for like microsoft.com, they could use R-N-icrosoft which looks like an m but isn't, stuff like that.
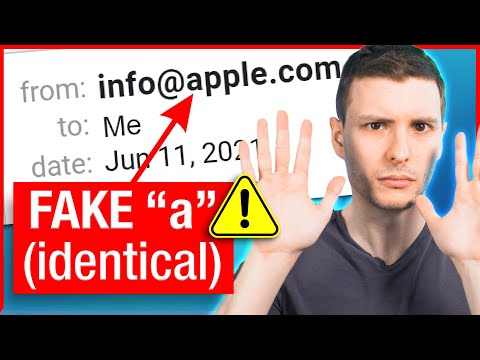
Check it letter by letter. There is another technique scammers may use, though is admittedly rare but still possible, which is using foreign characters in the domain. And you might not realize that domains can actually have all sorts of unicode characters in them, including foreign characters that look EXACTLY like standard latin versions. In 2017, one researcher registered what looked like apple.com, but it was not at all.
It actually had a cyrillic 'A', which was identical looking, but actually resulted in a fake apple.com that was indistinguishable. Because of this trick, web browsers now show the decoded version in the URL bar, which looks like this. That's great for web browsers, but email software might not decode it.
And in fact, I tested a bunch of them myself, and was not happy with the results. So to do the test, first in Gmail I basically created an alias that I could send from, which included a cyrillic A, the same one from that fake apple domain in fact. I then sent myself an email from that address and looked at it using Gmail on Desktop, Windows Mail, Outlook, the iOS default Mail app, and the Gmail app on Android.
With Gmail, it did not display any kind of warning upon looking at the email, nor did it highlight or change the character. However, when I copy and pasted the address into the 'to' field, it did give me a warning which is good, but it doesn't say which letter or anything. But really in my opinion, it should really warn you as soon as you have the email open. The default Windows 10 mail app offered no help, it didn't warn me or anything.
In Microsoft 365 Outlook, it does actually show a message that tells you the email has been sent by an "international address and contains characters from multiple languages." But it's not very obvious and I still think it should highlight which characters it's talking about somehow. As for the iOS Mail app and Android's Gmail app, neither of those warned me or highlighted them in any way.
So if you're really suspicious about an email, but the domain looks totally correct, you can use tools that are out there that will identify individual text characters. You can google 'Unicode Inspector' for this site as a good one, and if we try that example with the fake apple.com domain, you just copy and paste it in. Then it says they're all latin letters, except the A says it's cyrillic, so obviously a red flag. You can also google for 'ASCII validator', which will tell you if there are any non-ascii characters.
The standard ASCII character set only contains 128 characters, all just normal upper and lower case letters and some punctuation, no weird look-alikes, so if there's anything besides those basic characters, an ascii validator should spot it. But be sure the site is NOT including Extended ASCII, which does have some letters with umlauts, but at least those are still visibly different, only just slightly. So basically to sum up Step 1, yes, we are still on step 1, you want to be 100% sure, letter by letter, that the domain is exactly correct and the official one. AGAIN, this DOES NOT guarantee the email is automatically safe, because it could theoretically be spoofed. The point is simply that if the domain IS wrong, we automatically know it's a scam right away, but otherwise we have more to check. Alright now onto step 2, where we'll take a look at several separate scam techniques, so be sure to pay attention.
The first thing we need to look at is the 'reply-to' field. In gmail you can see this by clicking this little dropdown arrow near the sender's name, and it will bring up this box, where we'll also look at the other stuff here in a minute. The reply-to field is extremely important to know about. This field tells your email program to send replies for this email to a different email than the email address that sent it. Of course it does have legitimate uses, but many times, if a scammer is spoofing a domain, they HAVE to use a different reply-to address, because they don't actually have the fake email they said they sent from.
Here's an example. And just pretend this one doesn't have a big warning and wasn't caught by the spam filter. At first glance, it looks like the email was sent by loan.uk.
But if you look at the 'reply-to', it says some gmail account. The scammer doesn't have the info@loan.uk email, so they have to use a different email to receive victims replies at.
Also watch out, because the reply email might be made to look similar. In this other email, the reply-to address is totally different than the 'from' address, but they called used the same name in it as the sender name to make it seem less suspicious. Also sometimes they won't even change the reply-to address, but instead in the body of the email itself just include text that says "send a reply at whatever email". Or of course a lot of phishing emails don't try to get you to reply, but rather click on a fake login link, or download a virus, stuff like that.
So if it doesn't say reply-to some other email address, it doesn't necessarily mean it's safe. In any case, if it looks like the email came from an official company, but the reply-to is some free email service, it's a dead giveaway it's a scam. And again later I'll show you some clues for how to tell if it's a spoofed domain like I believe this one was.
Another thing I noticed is sometimes it won't say 'reply to', but just says 'to'. Normally that would be your email address, but if it's some random other email, it might have been forwarded with a list. Like in this one it says "recipients", but it could say anything, and that could also be suspicious, just be aware that might be why. Now if you're using another email program and wondering how to see the 'reply to' address, I have some bad news for you. I tested most of the major ones: Windows Mail, Outlook, iOS default Mail app, and Android default Gmail app.
Literally the only other one that makes it easy to see the reply-to address is the Gmail app for both Android and iOS, where there's a similar dropdown. In all the others, you only see the reply-to email is AFTER you click the reply button, which is really just unacceptable in my opinion. In Outlook at least there is a workaround, if you double click a message to open it in a window, then go to File > Properties, it will show a space that says "have replies sent to", which is the reply-to address. And also below it lets you see the headers which we'll look at later.
Now let's do step 2.5 you could say. We're still going to look at this info box in Gmail, and specifically the fields that say 'mailed by' and 'signed by'. These won't always be there, but they can sometimes reveal certain attempts to spoof emails. I'll explain how these are actually determined later though. You can see in this example, it's supposedly from Frank someone, and the email address is support @ some trading website.
But below, it says 'signed by' some russian website. Also above, it says it was sent 'via' the same russian site. If gmail shows 'via', it means the domain sending the email doesn't match the From address. There are legitimate purposes for this -- many websites use mailer services to send out newsletters and stuff on their behalf, but you should still be aware of what this means. And remember, this is in gmail, but not everything else might show this info.
That being said, this is really important to understand. That 'via' thing might not always show up in gmail, even if the domain and email is being spoofed, ok? It only sometimes shows up. You'll learn why later in the video but this is again one of those things where if it shows up, it makes it a lot easier, but if not, it's NOT a guarantee that it's safe and is real. For example here's one where this is obviously a spoofed email, but it does not show 'via', so just know that. Now again, there are two that might be here, both signed-by and mailed-by.
For now just know they sort of serve the same purpose, just in a different way. Just know that basically every major tech company like Google, Facebook, Microsoft, Apple, all them should have both of these, and of course they should say that they are mailed by and signed by an official website of theirs. Also any other major company worth their salt for security should have at least one of these, and again it should match. If an email has neither, it doesn't automatically mean the email is a scam, BUT, if it comes from a really well known website that should know better, yes that is highly suspicious. So in that case, check previous emails they sent you that you know are legitimate and see what those showed. If it is indeed signed and mailed by a domain actually owned by the company, there's a good chance the email is legit, but there is one more place we can check to be more sure.
So onto step 3, we can look at the email headers. Don't let that scare you though, it's way easier than it sounds. You see there are 3 major email authentication technologies out there, which are SPF, DKIM, and DMARC. You don't have to know what these stand for, but they basically provide a way for people receiving emails to check with a website to see if they really sent a specific email. If a website has it properly set up, which again, all major tech comapanies do for all 3, it makes it easy for your email client to detect and block fake emails.
Unfortunately, not all websites use these, and even if they do, some don't 'enforce' their policies, it's called, meaning the email could still get through even if they fail the checks, but that doesn't mean you can't still check and see what the results are yourself. So back in Gmail, they make it really easy. All you do is open an email, go to the three dots, then click 'Show Original'. And here you can see the three results for the authentication tests I mentioned before: SPF, DKIM and DMARC. They might not all three be there, but that's up to the website owner. So let me give you a quick rundown of these and then I'll explain these in more detail after.
So as I've said, if it's a major website, especially for a major technology company, it should almost definitely have all three of these, and they should all say pass. DMARC is the most significant and most powerful, because it looks at both the SPF & DKIM records, and has it's own tests too. So if you check these, and they say pass, AND you're sure the domain is actually the real one, not one made to look like it, it's probably a legit email.
For other websites that are big but maybe not a mega corporation, they might not have all three, but hopefully SPF & DKIM, and they both pass, as opposed to fail. There are other possible things it might say, like 'Neutral' or 'Softfail' which I'll explain later. But if the email shows that ANY fail, I would be highly suspicious. It either means their mail server was misconfigured (which is unlikely for a massive company), or it's a fake email.
If you're using another email program, you'll have to look up how to view the 'email headers' in your specific program, then you can do Ctrl+F to search for the terms 'SPF', DKIM, and DMARC, and if they're in there, they'll show the same results as would in Gmail. Not every email program even lets you see the headers, but I showed you before how to in Outlook, you open it in in a window, then file, properties and then it's down there. You can copy and paste the whole thing, or just do control+F. I want to be VERY clear here though.
These three checks are NOT "is this a scam" tests. Their ONLY purpose is to check whether the email originated from the domain it says, or at least was authorized by the domain. If a scammer registers their own domain, and sends scam emails from that domain, they can configure all those checks and it will show pass for all of them, but that just tells you "yes this was indeed sent by this scam domain".
So this is why I put so much emphasis on checking that there was nothing funny going on with the domain name in Step 1, because nothing else we do matters otherwise. And I'll say yet again, if the email seems suspicious enough, no matter what, just be safe and assume it's a scam because you never know, maybe that person at that company got their email hacked and is being used to send out legit emails that are still scams. In fact, I found one very interesting scam email where exactly that happened.
So check this email out. It was in my spam box, but it actually claimed to be from a .gov email, which is unusual. I did immediately know it was a scam because just by what it said in the body which was "oh you win 600,000 dollars", and I looked at the reply-to address and it was some hotmail address, so yea pretty obvious.
But I also looked and saw it said both signed-by and mailed-by erie.gov, and in the headers, all three checks passed. And yes I also checked for any weird characters, and nope they are all legit. So you might be wondering, how this could have possibly happened? Well I looked up the person's name and apparently they're the sheriff of this town called Erie, and that's their site. So I have to assume the simplest explanation, which is the guy got his account phished or stolen somehow, and someone used it to send out scam emails.
And if the scammer hadn't made it so freakin obviously a scam, they probably could have gotten a lot of people. Just goes to show that no matter what you see, some critical thinking is your last defense. Ok so now let me get into more detail about some stuff you might see when checking these fields. I'm going to keep it simple for now, and afterwards for those of you who want to actually know how these checks specifically work can stick around.
First, SPF. This helps verify that the server sending the email with a particular domain address is authorized to do so. However, it's the easiest to spoof to pass of the three, so a pass doesn't necessarily mean much, but a fail is definitely bad and not to be trusted, that means it is in no way allowed to send that email. If you're wondering, "Wait, how are the security tests spoofed", well I'll talk about that later. If it's neutral, it's basically the same as it not being enabled at all, which is just bad policy and also pretty suspicious. A softfail is the same as a fail and is highly suspicious, and means the domain owner said 'even if this check fails, accept the emails anyway'.
It doesn't 100% mean it's fraudulent, and could easily just be because the mail server is misconfigured, especially if they're using a third party mailer service, but still don't trust it too much. The only exception might be if there is also BOTH passing DKIM and DMARC records despite being a softfail. Next, DKIM. This tells you that the email has not been altered in transit, and was written by who it says it was. But again you still want to see DMARC with it, because yes it could be a passing DKIM record, but that record could be for a site that is not even matching the From domain.
So it's not a 100% guarantee, though I will say in my experience, it seems that DKIM spoofing is quite a bit rarer than SPF. But, you might see a lot that says fail and they attempted to do it. But if you really want beyond a shadow of a doubt, DMARC is what you have to look for. A pass technically should mean the email was not altered, and also will tell you who signed the message with an encrypted key. In gmail, it actually says "with domain" and then the website.
If you're using Gmail here is where you really do have an advantage because it allows you to easily see the true signer of an email. And with this information shown, you can sort of do a DMARC-like test yourself, by looking and seeing if the domain here is the same as the one in the From sender. That's called 'alignment', that's also what DMARC checks for, for both SPF and DKIM. However this is really important. If it fails, then don't even bother checking if it matches, because that's faked anyway if it fails. Only bother checking for a match if it passes, because if it passes that means there was a legit signature somewhere, and you just want to make sure that legit signature comes from the actual sender domain.
In other words, if it passes, then yes you can see the true signer of the email. But if it fails, that means they SAID they were signing for that domain, but they failed, which means you can only know that that is NOT the domain it came from. And if you're not using Gmail and using a service that doesn't show you all this information.
Then really you just have to rely on whether there's a DMARC record, and if there's not, then you don't necessarily want to trust it if it's suspicious. Now if it passes, but the domain is not the same as the From address, and not an official site by the company, it means they sent a valid certificate, but it has nothing to do with the site it says as being from. And by the way, if the signing domain is not the same as the From domain, whether fully legitimate and authorized or not, that's actually when you see the 'via' thing show up in Gmail. But again that only happens if it's a valid, passing signature.
Like in this example, the domain is obviously spoofed. But, because it failed the checks, Google doesn't know where it came from, so it can't tell you, and it does not say 'via'. So do NOT assume that it isn't spoofed just because 'via' isn't there.
You always want to make sure that there is an actual valid AND matching DKIM or SPF record. Next if you see fail, obviously don't trust it, because it means either the email was altered in transit somehow, or could be faked, and at best a bad configuration. 'None' means the sender didn't sign it, which basically means nothing. 'Policy' means it was signed, but not configured in a way that is acceptable, so basically useless.
'Neutral' means it's either not signed or had a syntax error. So really the only one you can trust is a pass. so basically from my understanding, even if there is not a DMARC record, IF DKIM passes, and the signing domain is an official one for the correct website, that should be fine, because that's the big thing DMARC checks for, called alignment, which we can see here ourselves. Also be aware that a lot of big companies have free email services that scammers can use to send out scam emails.
For example, Microsoft, they have one through Office 365. And I believe that sends out one via "onmicrosoft.com". So if you see one that says "onmicrosoft.com", just know that's not really from Microsoft,
someone could have set that up and sent out emails via that, and someone might say "oh well it's sent via Microsoft, it must be trustworthy", but NO. Anyone could have really done that, so don't necessarily trust it if it's not matching the domain that was sent. Speaking of DMARC, I kind of already just said what it does. It looks at the SPF and DKIM records, and makes sure they were actually testing for the domain that is shown to the user in the 'from' field, and not some other random domain. Because obviously it would be useless if a scam email claiming to be from Paypal.com goes out, but includes SPF and DKIM records for 'scam.example.com', those two might pass,
but have nothing to do with paypal.com. That's why DMARC is so critical. Oh and by the way, those 'mailed-by' and 'signed-by' fields in the other gmail window basically correspond to the SPF and DKIM records as passing. If DMARC passes, it means you can be pretty darn confident the email is at least not spoofed or faked, but again make sure you check the 'from' address for any look alikes.
But if it has DMARC and fails, I would be highly suspicious. It could be a bad configuration of the email server, or it could be a more sophisticated attack, like this one I actually found that claimed to be from the IMF, International Monetary Fund, but obviously wasn't. With this one you can see that the headers show the SPF actually passes, but the DMARC fails. And on the email page, you can see it says mailed-by and this "bouncev02" dot "inter-net" whatever this is.
And here, "mailed-by" corresponds with the SPF record. But this is not IMF.org, this is some random website. That's why it says 'via' there.
Therefore, obviously this SPF pass is actually a pass of the "inter.net" domain, not the IMF. So they actually spoofed the headers to tell email clients to check SPF for a domain that is not even the IMF. Luckily with this though, IMF does have DMARC, so we can see that it obviously is fake.
But even if it didn't, now you can go look and see if the 'mailed-by' or 'via' thing is there. And if it's another domain, especially if it's looking suspicious, could definitely be a scam. So by now you should have a much better understanding of what you can look for if you come across an email that you suspect could be fake, but might not be very obvious on the surface. At this point you you'd only have to worry about a situation where the company's servers or someone's email was hacked to send it out, which is obviously a possibility, but less likely. And now I'll go a bit more into detail about how exactly the different authentication records work.
With SPF, that stands for "Sender Policy Framework". It is MEANT to specifically just check that the 'return path' in the header, aka the original sending server, is allowed to do so. You see, whenever an email is sent by anyone, it includes a bunch of info as you'd expect, like the email address and domain it's supposedly from.
But anyone can just code their email to say 'uh yea I'm this person', so how can you tell? Well what a website can do, is create an SPF record in their public DNS records. These are visible to anyone who wants to look them up, and they also tell web browsers stuff like where their web server is. The SPF record basically say "only servers with these specific IP addresses are authorized to send emails with my domain name on them." So if you get an email from an email claiming to be from paypal.com, you, or your email program, can look at the DNS records Paypal.com publishes and see if the server this email
came from is on that authorized list. If it matches, it's a pass, and if it fails, the website can either call it a 'fail' which tells you to reject any emails that do not match, or a softfail, where the website tells you "eh even if this doesn't match just accept it anyway". Which is often used during testing, but kind of useless to keep on permanently. Next is DKIM, which stands for "DomainKeys Identified Mail". This time in the website's DNS record, there is a DKIM record containing a public encryption key that everyone can see, while the official sending server keeps the private key that no one else can see.
These encryption keys are created in a very special way, such that the private key encrypts data that can only then be decrypted by the public key, and also the other way around, where the public key encrypts data that can then only be decrypted by the private key. This is called public key encryption, and specifically "assymetric encryption". So what happens is the sending server takes the contents of the message before it sends it out, then 'hashes' the contents of the message, generates a unique string. Now very quickly, hashing just uses an algorithm that generates a unique string from some data, and ONLY that exact data will generate that string called a hash, and also, the same algorithm will always generate the same hash for that same data. It's just an easy way to tell if a file or some data matches the original, without even having the original.
Now, the reason you have to encrypt the hash, is because a scammer could just hash some scam message and send it along. But, if the authorized server encrypts the hash with the official private key, then you as the recipient get the message and generate a hash of the message's contents. You then take the encrypted hash that was sent along with the email, and decrypt it using the public key published on the official site.
If the hash you generated matches the one you decrypt that was sent along, you can now be certain of two things. First, that the message was not changed, and also the website who's public key you used to decrypt it MUST be the true sender. Because the way the keys work, you know that anything you can decrypt with your public key, MUST have been encrypted with the private key, that you know only the real website has. So it kind of does the job of SPF as well. Finally, how DMARC works, and it's easier than DKIM trust me. DMARC stands for "Domain-based Message Authentication, Reporting, & Conformance".
I sort of already touched on this before. But this is necessary because the major weakness of both SPF and DKIM are, from my understanding, that someone could basically send along an SPF and DKIM record that has nothing to do with the email the human recipient sees as the 'from address'. So people realized "wait a minute, we need to make sure SPF and DKIM are actually authenticating the address the user sees, which is basically the whole point". So if a website enables DMARC, which again is listed in the DNS records, it checks this, and also lets the website owner say what should be done about emails that fail DMARC.
The main policy options are to do nothing, quarantine or send to spam, or reject completely. There's also options for whether this applies to subdomains or not. At this point you might be thinking, if we have all these layers of security out there, why do we need to go through and check so much stuff ourselves? Shouldn't all the spam get caught? Well no. Not at all. According the site spf-all.com which is tracking SPF statistics, of the 140 million domains they checked, 80% of those domains had no SPF record at all.
And SPF record is usually considered the most basic bare minimum security. Now not every domain necessarily is used for email, and the biggest sites definitely use it, but still. But here's more. Of the 20% that do have SPF, only 32% use the strict method saying to outright reject failed matches. Another 33% use a policy that literally does nothing and is the equivalent of not checking at all, and a further 33% use one that's 'softfail' which may or may not cause a rejection depending on their DMARC settings, if they even have that.
Oh and the last 1% have a record that explicitly says "yea anyone can send emails on our behalf and you should accept all of them no matter what", which are all either terrible mistakes, or their goals are beyond my understanding, because that is literally giving anyone permission to impersonate your domain. Also, according to Data by a company called Farsight, only about 2.7 Million domains use DMARC.
That is a lot in absolute terms, but not compared to how many domains are out there. If the other statistics are right, then there are 26 million domains that have SPF records, so are presumably sending out emails, but only about 10% of those use the authentication record that's the best. Ohyea , and of those that do have DMARC, more than half don't even have an enforcement policy which makes it almost pointless. So that should answer the question of "why bother checking yourself". While many websites have these records, there are plenty that don't, and even many that do don't have enforcement policies to tell your mailbox software to block failures.
So then it's just up to your email software's spam filtering capability. I guess the one good thing is that scammers are probably most likely to try and impersonate the biggest sites, which are also the most likely to have the most thorough security records in place. But by now you should hopefully never fall for a spoof email again.
Of course, even if the domain address turns out to be legit, you better make sure you still know and trust the domain in the first place. That's all up to you though. So I hope you guys enjoyed the video. If you guys want to keep watching, the next video I'd recommend is talking about some of the newest scams this year, and that will probably be around for a while. So just click on that right there. And also if you want to subscribe, I make a couple new videos a week so it should be worth it.
So thanks for watching guys, I'll see you in the next one.
2021-06-13 22:02


