Confidential computing with SQL secure enclaves - BRK3157
Good. Morning everyone. Okay. Welcome. On the fourth. Date of lignite thanks. For coming. My name is Jakob Chumash I am program manager, and sequel team I work on security, features for simple server and Azure sequel, database, and with. Me I have Dean wells he's. A PM and Windows. Server. Based team he. Works on security, features. And Windows so, in this session we're gonna share. With you information, about, some exciting, and truly game-changing we. Believe data. Protection, technologies. That. We are introducing in, the sequel platform, by, leveraging what is called, secure. Enclave technology. And. A bunch of other technologies. That the dean's team has been working on in Windows so. That's why I invited Dean so that he can present. To you the Windows part, of our end-to-end solution. Ok. So. Let. Me kick it off by giving. You some context, here about. The problems, that we were trying to solve with, the technology, called always encrypted and sequel. So. Many, of you are probably familiar and, are even using. Techniques. Mechanisms. Features, for protecting, sensitive. Data, and. Database. Systems, in sequel, in, particular, addressed. And in transit, so we have fairly, mature technologies. That. Protects. Data address, protect, data and transit, transfer, and database, encryption as a prime example of, that, there's. A technology that existed, in the sequel server for, about, 10 years or, more we. Have tls/ssl. In. The. Desert supporting sequel server for protecting, sensitive, data, in transit so. Now the. Challenge is that the, protection, that TD. Provides, it, ends the moment your data is loaded back, from disk into memory right the, protection, that TLS. Or SSL provide. And at, the moment Europe your, database. Server, receives data from your application, right and after that the, data appears. In, memory, of sequel, server processes. In plain text right so, the problem is that until recently. What. Was missing, was. Mechanisms. To protect sensitive data and use, by. That we mean data that is used in memory, of the database, system during. Query processing, and that's exactly the problem that always encrypted technology, that we introduced. A couple of years ago is. Attempt. To solve right. So. -. Let's, double click on that so the challenge, the issue, that we are trying to address is how, to protect, sensitive, data, inside. A sequel, server environment. From. Powerful. Adversaries. Basically, high privilege, but unauthorized. Users that, includes. Database. Administrators. Administrators. Of machines hosting sequel server cloud, operators. Or, anything any, malicious process, that may have, infected, the, hosting. Machine the environment. That has your database, right. Now. The challenge, is that. It's. Relatively, easy to achieve protection. Of sensitive data in use if this is just your only goal right, you, can basically ensure that the data that. You store in the database gets encrypted, before it is stored in the database using your favorite, encryption, algorithm, like AES 256, for, example, the challenge is that once, you do that you have compromised. The. Query. Processing, capabilities. Of your database environment. And sequel server and in database, system will not be able to compute. Performance. Of. Your data process, your queries, right so, that's that's what we don't, want so, ideally, our goal is to achieve what we call, confidential.
Computing, Or computations. Without seeing the data with, one sequel, server process, to, be able to perform. Rich computations. On the data pattern matching arithmetical. Operations whatever, you can think of sorting, or. And so on, in, such a way that the data is never ever exposed, in plain text to the potential, attackers, in. In, the server environment. So that's the the challenge that we that, we are trying to solve here so as you can see we trying to achieve two goals that are until, recently, have, been kind of mutually, exclusive, but not achievable, together. And on one side protecting. Sensitive data news from, these powerful adversaries. On the other hand ensuring. That the. Sequel server can continue, support. Rich functionality of, sequel queries okay so. About, two years ago he made the first step towards this vision. Okay. And. This. First step, was. The release, of the first version of always encrypted in sequel, Server 2016. So. Let, me how many of you are using or are familiar with always encrypted that we shipped in in 2000 ok quite, a few hands so, let me make sure that you, know we are on the same page because I want to. We. We need to understand. The. Mechanics. Of. This. Always. Encrypted. Workflow. And and and, technology, so. That we can dive, into how. Unclips. Enhance. It. So. Always. Encrypted as a client-side, encryption it, works by encrypting decrypting, data on the client side right, so what this means that as you can see in this diagram the. Data is. Appears. In plain text on the on the client side the client application owns. The data but. The moment the data leaves the client application the data gets encrypted okay, so, the sequel server never, sees. The data in plain text doesn't, see the. Keys that were used to encrypt the data and, client X either right. So. This, client-side, encryption has, two other important. Properties, one, is the encryption transparency. So. This. Encryption, decryption happens. Inside a client, driver a da-da-da-da, the BC JDBC. And. That, client rather transparently. Encrypts, decrypts, data it figures out transparently. Which, data needs to be encrypted before it is sent to the database and, which. Query results, need to be decrypted, so the application, doesn't have to call crypto, routines explicitly. To. Trigger these crypto operations, so that makes programming, an app development, easier. The. Other key property, that as I mentioned earlier this initial, version of always encrypted was the first step towards. Achieving, the confidential, computing, vision right so. In this initial, version we managed. To support, some. Operations. On encrypted, data to be precise it is just, one type, of computation. Namely. Equality, comparison, and when. We achieve that by. Using what, we call deterministic, encryption so, the terroristic encryption, is the type of property, preserving. Encryption, which, ensures, that if you have two. Values that are equal to plaintext. Values after encrypting, those values, the resulting, ciphertext values. Are also equal, right so, what this means is that sequel. Server now then can, reason, can can. Deduce. That to, plaintext. Values, are the same by, comparing, their ciphertext, doesn't, have to know the underlying plaintext. Right so, this is very basic and very simple, but, surprisingly, in database, systems in sequel, there, are quite a few. Types. Of queries that leverage. Just equality. A person, that are quite useful so. Point. Lookup searches, are one example equality, joint is another example we. Also can support simple aggregations, using group by operations, okay so. That's that's what we did about two years ago and that was our first step towards, this confidential, computing, vision now let me, double. Click and, and do. A spent, a few minutes on this. Architecture. That exists. Today which. We're going to build on top of to. Support, more. Functionality. With secure Enclave, so. Although encrypted is a those. Of you who who used it know it's, a column level encryption so you choose individual, columns to be encrypted and they. Are encrypted, do it what we call column encryption keys these are symmetric, keys and we are protected, with symmetric, keys that are called column master keys. And. It is many-to-many relationship, we can have many columns, many, keys right now the important, thing to to, notice, that.
Neither. Keys, are visible. To. The database, system right so, you have column master keys which are stored in the encrypted, form and the database, metadata, and ever in plain text and you have master, keys that, are under, control of the application, so the application. Is. Responsible. For managing those keys and we. Support up the out-of-the-box the, ability. To store those keys in windows certificate, 8 storage or key vault HSM. Devices, you can also choose, to store them in, a custom. Key store right now. Let. Me walk you through. The. Typical. Query. Processing, workflow, for always encrypted so. Index in this example on the right hand side you can see a table with two columns encrypted. On the left hand side you have a client application that. Is trying to issue a point lookup query right so it's we looking for a matching, name, for a given social security number which is a government ID in the US, and. These. Two columns are encrypted, on the server side right so, the first thing that normally. Would happen in this case the client driver, after receiving, this query would just send it to the sequel server submitted. For processing, right now, with always encrypted in place, instead. The, client driver will make transparently. This. Data. Metadata. Discovery. Call via. By, calling the store procedure, called LPS P described parameter, encryption, so, what what, is happening, here the driver, submits, the query statement, that was. Involved. By the application, and the sequel server analyzes. Statement, parses. It and analyzes, it to figure, out which parameters. Query. Parameters, in the statement, need to be encrypted on the client side so, basically it concludes, in this case that the SSN. Parameter. In. This query happens to correspond, to the database, column, as, we just encrypted, so, what it does it responds, with all, the, metadata, all the information, it knows, on, how, this, column is encrypted, so this is the key parts on how the way to describe, all is encrypted is to say that this is a encryption. Technology, that is informed. By server-side. Metadata, client-side, encryption, informed. Controlled, by server-side, metadata, so the server knows about, which, columns are encrypted, how they are encrypted, and it. Supplies. This information, dynamically. To the driver so the driver now. Knows. What, to do so the first objective of the driver in this workflow is to, decrypt. The column encryption key, that is stored indeed encrypted. Form on the server side and in send back in this response, to the, client so the client knows. Were the master keys from. The field that is called here, column. Master key path so, it reaches, out to the key store, called, the unwrap operation, decrypt, operation, on the key store now it has a column, encryption key, data encryption, key in plaintext and what, it can do it can now encrypt. That query parameter. That as a sent value rewrite. The query statement, not the query statement, but the query invocation, and. Replace. The plaintext with the cipher text so what the server gets is ciphertext. Of. The, query, parameter, that corresponds, to the encrypted column and assuming, Dda that the SSN, column is encrypted using, deterministic. Encryption a, sequel. Server can evaluate, this, equality, comparison. In the work loss right, so. That's that's, what, I mentioned. Earlier that's how we support.
Equality, Comparison. Via deterministic, encryption so. Now. The. Sequel server found, a matching name it knows, that this. Value, comes from the encrypted column and therefore it, attaches, again. All the metadata, that informs, the client how this column is encrypted, which, allows at this time to, decrypt. The, name. Value from the result set presenting, plaintext, to the application, right so, what you get here to. Kind of main takeaway. From this slide all. This complication. Workflow. That you see on. The right-hand side of this of this diagram or, this complexity, is hidden, from the application, point of view right it, sends, a query submitting. Plain text data and receives. A. Plain. Text response, a plain text result set that's that one key key. Point the, other thing is that because. Of, deterministic, encryption we, can support. Some. Types of queries like equality. Comparison. In, endpoint. Lookup searches, so, that's that's how it works today you. Have a question. Right. So the question is how sequel server know which data should be encrypted so I'll show you that to. You in a in, a demo in a second basically. When you define. This. Is part of your table schema, so, your table schema contains, the information about which columns are encrypted, and how they aren't encrypted, so, when. You define a schema, you, would, designate. Some, columns as encrypted, okay. So. That's, that's what we have today now, you may say okay equality, comparison, that's, great, I can do point lookup searches, I can do equality, joints well, for, many applications, and we got this feedback from customers in, kind of we knew that up front at. The time we even shipped this initial. Version of always encrypted equality. Comparison, is not sufficient. For many, types of applications, right if you have an application that processes for example. Rich. Personal. Personally. Identifiable. Information. Like. Names addresses, phone numbers and so on there is a chance you want to do more than equality, comparison, you may.
Want To do point lookup searches, or or sort, these values, or you can you. May want to perform. Arithmetic. Or, computations, on some sensitive. Numerical, data right to. Achieve that today with always encrypted, the current version of any, other encryption, technology. Protects data and use in fact you'd. Have to modify. Extensively. Your applications. So that they pull, all the data from, the database and re-implement. Your it business logic on the client side and, if you have sufficiently. Large data set they will just not scale right it. Will be extremely hard, for you to achieve that so, that's. What I meant, earlier when I said achieving, these two goals protocol. Sensitive data and use on one side and and preserving. An. Ability, to perform rich computations, that's something something. That is very hard so that one problem the second problem is more on the operational, side for those of you who use always encrypted, in. Sequel server 2016. 17 or usher sequel database you, know that, in. Order to perform. Any, cryptographic, operations, on. The data for, example to encrypt your data for, the first time or to rotate, column encryption keys, right. You. Have to move all your data outside of the database again perform. These operations, on. A different machine and, then. Upload, the data back sequel, server cannot, perform, these operations for. You by design, because it doesn't have access to the keys right so. That's again as challenging. Both, from. Performance, reasons also from the compliance, security reasons, now you you. Need to have this this, other machine that is part of your compliance, security domain, which, can safely. Access. Encrypted. Plaintext. Data in fact than encrypt re-encrypted. Right. So. These are main, two challenges, that we are trying to solve and. The. Technology, that we'll use to, to tackle these these. Hard problems is called secure, enclaves. So let me spend a few minutes explaining what, enclaves. Are how many of you actually have, heard about technologies. Like Intel SGX. Okay, a few right. So. An. Enclave, is is, a. Special. Region of memory it's. An isolated, protected. Region of memory which, is of course part of. Containing, process, and it, has some really cool special, properties. Right, namely. It is basically. Not. Accessible. To not. Just. The containing, process, but everything. Else on this machine all other process, processes, and the OS itself, so, basically, it's a black box that, cannot. Be accessed, by. Administrators. Operating. System, other processes. And/or the containing, process, on, that machine okay. And. It, runs come. In contain of course called and data and that. Code needs to be signed, in a special, way to run inside the Enclave now. There. Are several, ways to to. Achieve. Enclave. Isolation. To achieve, to protect, the Enclave memory and. Different technologies achieve that in a different way we. Can categorize, them in general in two buckets, so some, of them are Hardware technologies, and intelligence. Or, arm. Thrust, zone are examples, of those so. In the case of hardware technologies, the isolation. Of the hardware. Or the of the Enclave is provided, by in case, of Intel. SGX for, example, by the CPU, itself and, the Enclave memory is encrypted, and it's. Therefore, the. Data in it the code in it are not visible for, anything else on the machine, the, other technology.
Or The other types of technologies. Leverage. Hypervisor. On the machine and in this case a hypervisor. Is the entity that guarantees. The security. And the isolation. Of the arc length and, virtualization. Based security enclaves, in Windows. Our example. Of this. Approach. So. To, give you an idea how. What, what the experience. Would. Be if you try to access, the memory of a VBA's Enclave. This. Is the screenshot that. I took when, I opened. After I open a windbg. Debugger. And I connected. To a process, that contained, the Enclave, and I found the Enclave memory. So, I was. Pretending. To be an attacker that wants to exfiltrate. The. Data from the Enclave right so this is what I could see the question, marks I was not able to see the, actual data so. Similar, so if you perform, a memory scanning, attack you won't be able to see the Enclave memory if you take the memory dump you won't find the Enclave memory ended down right so, these are key, properties. Of unglazed. Then, make them very, attractive. Technology. To. Serve as trusted. Execution environments. For processing. Sensitive, information. So. That's, exactly what we, are using. And, the upcoming. Version of always encrypted code. Always encrypted with secure enclaves, we're, actually very excited. About sequel. Server 2019. Which on us was, announced, earlier this week, there. Is a public, preview of, sequel, server 2019. Already available to you and it does include, always, encrypted with secure enclaves, we. Use VBS, enclaves, in. In. The current version so. You. Can now all, of you can now, see. And try and test it. So. From. The security, standpoint the goal of always encrypted with secure enclaves, is doesn't. Change the, goal is still to protect, sensitive data from high privilege, but unauthorized. Users, okay you, don't want DBS machine admins and so on to see the data what. We want to improve, on or. Is. Functionality, so, we want to preserve sequel, server ability. To process rich. Queries, we, want to support in place encryption, so that you don't have to move your data outside of the database right so, this is how we're gonna do that so we. Have modified. Sequel. Server so. That when it starts, it loads a VBS, Enclave, so a sequel, server now it's a hosting process, that contains, an enclave, write and this. Enclave, runs. The code that. Is responsible, for evaluating, certain. Expressions. In sequel queries. So. And, this Enclave essentially, acts as a as, an, extension, of the client, on the server side you can think of it as a trusted, representative.
Of The client, application, within. The sequel server environment. It's like an Li, behind, enemy, line, enemy, lines or like like. A foreign, office in a given country right. It's. An extension of the client side trust boundary. And. The, way we use the, Enclave, is during. Query processing, sequel. Server delegates, certain operations. To. The Enclave, that now being, a trusted. Execution environment, can, safely, decrypt. The data and, perform. Computations. On plaintext. So, that opens, up new possibilities, we. Can support, in. General all. Kinds, of queries we, starting, with a few that. Some. Of you and other customers, have asked for and that's, our top priority, so we want to support in the current version in the, current preview version of sequel server 2019. We support, rich. Queries, like. Like, predicates, pattern. Matching range. Queries, we're, still working on indexing, and I, will, I can. Tell you more about our roadmap, in. A future in the next slide in. One of the next slides our, roadmap, for for the next milestone, next releases and, one. More thing that gives us in place encryption, right so, with with our case we can also delegate, cryptographic, operations, to. The arm clave so you don't have to move your data and, use, tools like always encrypted with order the power show that, run on the client side you can the. Amplify, and perform, these cryptographic, operations, for. You locally, a securely. Inside sequel, server there, is a question. Yeah. So we'll talk about it more I repeat, the question the question is are. There any specifically, requirements, regarding. The version of Windows or, hardware. So. Yes there are specific, requirements, regarding. In. General, I think the correct answer is both, and but, the Dean can elaborate, on that when. He. Talks about attestation. This. Technology, is available in the latest version of Windows Windows Server 2000, 19 and its client, counterpart. Which is called, Windows 10 version, one, eight zero nine if I'm not mistaken okay. And, regarding. Cardle we'll talk about it we'll recommend, that your machine is equipped with TPM. 2.0, for production. Purposes you. Don't have to have it for, testing, we'll get there okay. Right. The. Question is what's the cardinality, of relationship.
Between Enclave. And and, sequel server so. Sequel server contains, just one Enclave, the Enclave is stateless. So. No. Not, quite stateless. But it, contains, information, about, sessions. I get, to that in a second but it's one per sequel, server process. Okay. All. Right so. I just told you that this. Enclave, is responsible. For processing, sensitive. Data and it's, capable of decrypting. Sensitive, data and can. Operate on sensitive data in, plaintext. Right, so. And, it's an X basically, and the the, Assumption, here is that the. Enclave is is an extension, of the client-side, trust, boundary, that the client can trust the Enclave, that this Enclave is a is a trusted, friend of the kind application, but how, do you know and how does the application know. That. That's, true that that. This Enclave is, a, trusted. Friend not, an enemy right that. This, Enclave doesn't, run perhaps, a malicious, code that. Publishes. Your sensitive. Data on a file, sure or. To the internet directly or indirectly right. So. That challenge. That problem. Is addressed by. What. We call unclick, attestation. Which. Typically, involves, the. Client, application or. And, sequel. Server, interact. With an external, service called, an attestation, service. And the role of the data station service, is to certify, to prove to the client, before. It that attempts, to use the Enclave, before, it authorizes, the use of the Enclave it. Proves to the client, that the. Enclave is trustworthy, it's. Real VBS. Or SG exam clip for example and, it runs the code that you can trust and Dean. Will spend about 15 minutes to talk about that, after. I I do my demo in a moment okay so, that's one common, question that pops. Up the, other question, you might be thinking about is. Okay, so I just told you that sequel, server never, has, keys. In plain text right and, I also told you that the. Enclave inside sequel. Server. Decrypt, the data right. Or re-encrypt. Data so, the question is how does the Enclave get the keys if it's part of the sequel server process, but, sequel doesn't have the keys in plain text so this, challenge is addressed, by, the. Client driver, creating. A secure tunnel or a secure, connection a secure session to. The Enclave, so, this is done transparently. During, normal. Connection. Setup process. Using. TDS protocol, which we have enhanced. So. During that part, basically. The client and the, Enclave, negotiate, a shared secret using, diffie-hellman protocol. And now they have a sure, secret, that they can use to, that. The client can use to, encrypt. Column. Encryption keys, that. Can, now be securely, passed to the Enclave, so the young clave can perform cryptographic operations on, the data and. The, client also signs. Queries. So, that we have guarantees, that only. Properly signed queries, can be executed. Inside in our case so there are some, security in depth protection, that we have added as well okay so. With, that let. Me show, you a demo of what, is available today in, sequel, server 2019. Okay. Right. So the, question is how how much RAM is allocated, to the Enclave. So. One way to answer your question is that so, today in sequel, we. Don't allocate a specific amount, of of, memory, we, kind of let the Enclave. Grow. Dynamically. With. VBS, enclaves, that's very easy. There. Are there is no limit, for the size of the VBS, Enclave, with SGX, and. There. Are much, stricter. Or the. Limitations, regarding memory, size exist, but it will even, with SGX we can we can work with fairly.
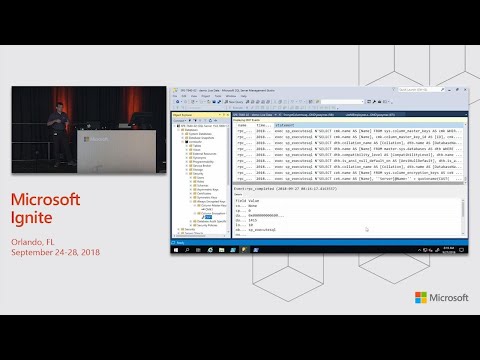
Small Enclaves, so. The size is not an issue with. VBS, it's not an issue because there. Is no limitation. In. Fact okay. Right. Which. Number am I here for I think. Okay. I guess I'm not connected. Sorry. About that. Alright. So. For this demo I'm going to use a very simple data set it, has just one. Database. With one table so. Let's see what this table contains, it. Contains some, information, about employees, Social. Security numbers and salary, figures is, the sensitive, information in, that table. And. Right now I'm wearing, a heart of a database, administrator I, can see all the data in plain text without any issues right if, I'm a machine admin, on this, on this machine or if, I'm malware, I have been even, more means. And ways to exfiltrate, the data I can scan memory or I can, generate. A dump file and know that data will be there in plain text right so, that's that's the starting. Point for this demo now I also, have a web. Application which. Is very. Basic, dotnet. App that, displays, all, this data, and in, addition to that it allows me to do some filtering, so. I can filter these employees, by salary range or I can filter them by, sub by a portion, of a social security number and now, if I let's. See if. I if I use this application at any point of time it triggers a sequel, query, so. Let's see how, this query looks. Like from. The sequel server, point. Of view so. This is what sequel server gets right it, as. You can see it's a fairly rich query it contains, like, per decade on the SSN column range comparison, on the salary column right. So this is the goal for. This demo I want, to protect my sensitive, data and use I want to make sure that, high. Privilege but, unauthorized. Users users, like, DBAs, on. The server machine cannot, access my sensitive, data in plaintext but I want, to do that in such that allows me to keep this application, unchanged. Right I want, this particular, query, to, continue, to run in the unchanged, form okay, so that's. That's, the goal I don't, want to reengineer, my, app to load the data, replicate. This computation, on. The. Application. Side okay, so. Let's, do that and we'll, do that by, configuring. Always. Encrypted using enclaves. For. This particular, table. So. The first step for. You. To use always encrypted I'm skipping. The setup part which, is not that exciting, here so there is a bunch. Of, always. Level configuration that, you need to do and Dean. And I will talk about it later on but after, you've set it up the. First step you would do in sequel server is you. Would create, a column, master key right this is the key protector, that we use and always encrypted. Actually. Have already created a master key is a certificate, in the local machine store, on. This machine so what I'm doing now I'm basically creating, a metadata object, inside sequel server that describes, references. This master key which is a certificate. So. Let, me do that and there is one little detail I want to highlight. Here. So, this I'll allow, Enclave, computation, checkbox it, I. Check. It I selected. To. Express. My intention. Which is I want column. Encryption keys, that will be protected.
With This key protector, with this master key, to. Be permitted to be used inside Enclave, computations. Okay, so. Let's. Do that let's complete, this dialog. So. I can briefly show you what this did. To. The database. So. This. Is the, script. For, creating, the metadata object, I just created using this UI as you can see this there is this unsafe computations. Property, and the results of signature, that, was dynamically, generated, by this tool. It prevents. All that metadata, including. This property, from tampering, so that you. Know if you don't want as a data owner for, your data to be used in Enclave computations. You, have a mechanism to, enforce it, right so, that that signature, achieves. That okay. So. We have a column master key what, else do we need we need column, encryption key, right to, encrypt, our data so that's gonna let's. Again. Name the metadata object, that is describing, it let's, click OK multiple. Things happened. When. I clicked okay the, plaintext CK got generated. It was encrypted, data encrypted with the master key and uploaded. As a metadata, object, to the database, okay so, now I have, a keeper, and. Let me try to encrypt, them so. Now for, those of you who are familiar with the current version of always. Encrypted what would you do to encrypt your data what do you do, which. Tools do you use what's, your favorite, tool do you have to to pick from. SSIS. Is, one option so maybe more than two, always. Encrypted wizard, and sequel server management, suit your PowerShell, so, with always encrypted wizard, you, basically go here and in, open. Encrypt columns, and he would complete this this. Wizard at the, end that would trigger. Time-consuming. And, expensive data, migration. Operation. Would move all the data from, the database encrypted. Uploaded, back we, don't want that right, instead. We want to encrypt this data in place and. With. The changes, we have done in sequel, server 2019. You can do, these operations using, plain, boring. Alter, table. Alter. Column, syntax, you. Can do all that in, T sequel there is one condition however, now. You're acting as an owner of the data right so. Which, means that you'll be encrypting, it and that. Means that you need to have access to the keys right so, there are certain, competitions, that you need to meet. So you need to run this operation from the machine that has access to the master key, in addition, you need to ensure that. Use. Your. Always encrypted is enable in the database, connection and that. You specify. The. Endpoint, of the other station, service, that, will be used to verify the Enclave, before, in place encryption, actually happens okay, so, again that's something that we'll. We'll, elaborate. After. The demo okay. So. Let's run this this, script, okay. So, it's completed instantly, partly, because I have a very small data set but mainly because all this operation, this. Cryptographic, encryption. Operation. Happened, locally. Inside sequel, server no, data movement, was. Involved, right so, how, do we know that the data actually was encrypted so, now back, to my first. Query. Window you, can see the previous results, of it right so, let me now rerun it okay. So. Now as a, DBA, I can. Only see SSN. And salary values, encrypted. Right and, sure. If I change. My, connection. Properties and, if. I specify. You. Know. This. Flag, for. This query window I will be able to decrypt the data but. Only. Because, I I have the master key on this machine if I do the same thing on a machine that doesn't have the master key I will get the failure I will not be able to get access to plaintext. Okay, so. Now we, have the data encrypted, let's. See, how. Our web, application, got impacted. By putting. Encryption. In place inside, the database so, let me, refresh. This up. So. As you can see it still shows data it, actually, shows the SSN, and salary, columns, in plaintext and this, is because this application has. Been already pre-configured, with, these, connection. Properties that I showed you in SSMS, so always, encrypted, is enabling, the database, connection. So, what it does it turns, transparent, decryption. On in this case the. Results, that are retrieved, in the encrypted form the driver transparently. Decrypts, them and shows plaintext, to the application, right so, that's why the application. Can see, the data in plaintext because, it has access to the, keys okay but, not only that the most important, detail here is that these. Filtering, capabilities. Filtering, by salaries, filtering. By Social. Security number, portion of it still work right, so let's, see if, and. How the, queries, these applicators. Application, issues. Have. Changed. So. I will go back to my. Extended. Event session, and. I will show you.
How. The query, that sequel, server gets, looks, like now okay so. Two, things to note here no. Change to the query statement, this is the same rich query that you saw before, despite. The fact that my two columns, are encrypted, now and sequel. Server doesn't have accessed, the untrust, portion, of it it doesn't have access to plain text it. Can process. It right. The, second thing to note is that these. Search, criteria. Query, parameters. The, sequel server gets, them India encrypted, form now because. Again the. Usual. Always encrypted, workflow, kicks in and it causes these, salary. Minimax. Assessment. Pattern parameters, to be transparently. Encrypted, inside the client, driver so. The sequel server gets, parameters. In the encrypted form has, the data stored, in in the employees. Table and the encrypted, form it sends, this data to the Enclave, Deonte safely, decrypt, the data and, can perform comparisons. Or. A. Pattern matching, on plaintext, oh so that's that's how it works so what I achieve, this I managed, to protect sensitive data in use from hi traders users, and at the same time I've, done. That without changing my, application, queries I didn't, have to reengineering, application. To log the data and, perform. Computations. Locally, okay. So, now. As. We, said earlier, all. That works with, the assumption, that this Enclave, is a, trusted. Entity okay. That. It's a trusted. Representative. Of the client application, on. The server side so now how, do we know that that's truly, the case okay how does the application. Get. This assurance. So. Now. Deana I will walk you through. Through. The workflow of testing. The Enclave maybe after you, explain. What. How. It works. Alright. So. What, we're talking about here is this, is a service whose purpose, in life is. Become. A role in Windows it's been there since Server 2016, and it's been matured in Server 2019, and its, purpose in life is to sit in a physically, secure data somewhere data center somewhere and attest. To the health of other. Workloads, the. Process of at attestation, is I, take, measurements, from something, typically, they are cryptographic, measurements. And then, I compare. Them against, a pre-configured, whitelisted. Policy, and that, gives me the ability to, say healthy, or unhealthy.
That's. Basically, what the host Guardian service does now. It does it currently for precisely two. Workloads. The. First is for hyper-v, we, use it for a technology that I also own called shielded VMs and we, use it for sequel, always encrypted with enclaves, so. We. Expect this model to mature right, now it's a Microsoft, only thing we will eventually expose, it so other people can write Enclave. Binaries, and leverage this trusted, execution environment, but for now it's a Microsoft only thing the reason it's Microsoft, only is because we haven't yet built like a code signing portal, or ways of figuring out if the binary should even be signed because, I don't really want somebody writing a binary that's got a built in virus, us then signing it in a code signing portal, of them somebody giving it implicit trust because. It runs inside an Enclave so, we've got some work to do now that the technology is working for us to ensure that we can offer this to third parties. So. You now know what the process of attestation looks like. I want. To tell you exactly how it works now with my regular audience I tend, to get a roomful of IT security geeks, my, suspicion, here is I don't have a roomful of IT security geeks, I have a room full of DBA geeks would, be my guess so. What I'm gonna do is wow you with science you may not understand, but hopefully, you'll. Walk out of this room saying this isn't security, theater this is genuinely, strong, security. Controls put in place by windows, to, prevent malicious. Software, or, even admins. Running. On a host where the data physically, resides with them from, even getting into that data that's, the goal so. How do we identify a. Sequel, host that is legitimately. Allowed to, process, this database, decrypt. Keys how do we do that could, we identify it, by a name or a serial, number on the motherboard or an, Active Directory domain, joint account we, could use all of the above what, we chose to use was something extremely, strong we. Chose to chose to use the TPM, who's, heard of the term TPM, okay. That is most of you great so, a TPM, is a trusted platform module it is a tiny little microchip, that runs typically, on the motherboard of most pcs these days it runs in laptops, and in servers and it, is used as a way of securely. Sealing. Keys. Ceilings. An interesting, term and I use it very deliberately, its keys secrets. Anything, really but it's typically very small pieces of data so often time the secret is a key or a password, the. Process, of sealing goes like this and this is where we get a little bit deep so we'll do it relatively, slowly and feel free to ask questions as I go through this if it's relevant but, again this isn't massively, important, that you understand, how it works end to end but, it's cool to understand, the security assurance strength, that comes from it when.
A PC boots these days you've got two biases, that you could choose from the old one is called peek at or PC a T bios that's, what we used to use years ago the, way that that would boot is the machine would be powered on with the big red switch it, would read the bios off of a ROM it, would run that bios that, bias would eventually finish setting up the hardware and it would then go and look for the first boot device based. Upon the controllers, and the disks it's using it, would then go to a logical, sector of about 512. Bytes in length read it and then without any regard, for what it said run it, that. Sounds incredibly, secure and difficult to attack doesn't it that's, the way things used to work and that was very very easy to, insert a rootkit because, all you had to do was change that first 512, byte sector, make, it go and run your component, that got into the computer first it. Then went back to the original sector. That it had moved and then the rest of the operating system loaded with this nasty little rootkit, looking up at it going I can see everything, you do and you don't know I'm here. That's. The purpose of a rootkit that's how they work they, get there first and then everything else doesn't realize they're there while it looks and inspect everything they're doing that's. The past it, doesn't work that way anymore the, reason I'm pointing this out though is because a lot of machines still ship from vendors today with support, for both types of firmware peek. At the PC 81 I just described all UEFI, the. Unified extensible firmware interface UEFI. Is the, new one a lot, of machines switch with PC 80 or peek at switch on and you, have to turn on UEFI, for, this particular feature to function you need UEFI. Firmware, the gentleman here, ish I believe asked a question about the hardware requirement, was that you I don't remember which and. Was somebody, yeah so, you need UEFI, firmware, for one you. Need a TPM, v2. TPM. 1.2, is simply something that we could have supported but, we chose not to the, reason we chose not to is we would have had to rewrite the entire attestation. Mechanism, for each version of a TPM so. When the variant causes that much work and the. Version we're going to support is the later and greater one it makes sense for us to not look to the past so, this was quite literally resourcing, we could have done it with the TPM 1.2, we didn't we did it with what's more modern more secure, you. Also need some very, specific technologies. In the platform, typically, referred to as VT X or virtualization, extensions. Most. Machines that you would buy that you would run sequel, server on these days will have that support for free in many cases though it's not switched on so you, would actually have to go into the firmware and potentially, switch on Intel. Virtualization, extensions, which is what VT X stands for the reason, we're doing this is because the entire technology, that, Jakob, had described, earlier on the trusted execution environment, the Enclave it.
Achieved By using the same technology, that hyper-v. And VMware, and citric, Xen and Amazon, and aja used. To keep an isolation. Barrier between two VMs it's, exactly the same technology as that it's no different at all so. Instead of guaranteeing, that VM one can't inspect VM two and vice versa and so on we, guarantee, that we can compartmentalize. And, isolate, the operating system components such, that this tiny little ki te e trusted, execution environment, can live quite safely, and even kernel-mode components, in a, legitimately, booted, scenario, can't, see inside it even, the kernel can't get in there and that's. One of the key things that people struggle to take away the kernel is not the master of this system anymore the, hypervisor, is so. The question then becomes if, I've got UEFI, I've got TPM, I've got VT X and I've, got Windows, and I've just said that even the kernel can't get in there well, I could argue that well. The kernel can get in there what if the machine is not being measured what if it's not got an attestation Authority, now, if somebody breaks our software, model and they. Manage to get something in before the hypervisor now, everything, I've just said is rendered moot. So. What was the point of building it all well the point was we have to have that to, implement it in software and to implement it in today's hardware but we need to make sure it's running as it was designed, that's, where attestation comes in sequels. Doing all this magic, to all this stuff going on with VBS enclaves, Windows Server 2019, is using all these very clever virtualization, security, extensions, to make this trustworthy, execution, environment, exist and somebody's, circumvented, all of it by installing a rootkit well. We. Can't detect the rootkit unless somebody's, looking for it unless somebody's measuring, it and knows what a definition, of health looks like that's, where again the, attestation process comes in so, first things first we have what a box we've got sequel turned on we've got UEFI, firmware, we've got a TPM, v2 all, of those things happen and you've got Windows Server 2019, installed now, I want to make that machine work, with a hosts Guardian service so we can attest it as healthy the, first thing I do is I extract, a key from, the TPM it's called an endorsement key. Every. TPM, outwear has an endorsement key a public and a private keeper, we. Extract the public, we'll use that as the identifier, so, we ship the public key from the TPM over, to the hosts Guardian service this. Is not like a shared secret this is typical asymmetric, cryptography where, one key can be used to encrypt and the other key can be used to decrypt and for those who aren't familiar with it it doesn't actually matter which way around you do that if, you encrypt it with the private key then the public key can decrypt it and there, is actually a reason for that we use that for signature, purposes but typically the public heat encrypts, the private key decrypt where, do you think the private key resides. Forever. And eternally, inside the TPM it will never release it it will release data that it decrypted, with that if it's deemed appropriate, to do so but it will never release the key so.
When, The machine needs to become registered, with the host Guardian service you've, one time and one time only you extract the EK pub the endorsement, key public from, the TPM and you give it to the host Guardian service what you've now achieved is you have identified, a legitimate, host it is, not yet blessed, what. You now do is build the operating, system on that host to the point where you consider it to be perfect. It is, your golden, image with, sequel, and with DB admin tools installed, anything that you want you make, it box, that, is built perfectly to, your golden image please, don't put you know debuggers, and malware. And viruses, on there otherwise we'll consider those to be blessed because we're about to say that's, trustworthy, so, if you built it with a virus and then, you tell the tool deem, this trustworthy, it will literally record the virus as being trustworthy, ok, so build, it with the perfect set of tools you, then run a process to go and scavenge all that information, from it and we. Record that information the. Vast majority of what recording, what, we are recording rather isn't every, single binary on the disk it's, those that constitute, the boot path and this. Is where I want you to understand how thorough. This, is so. When the machine boots up UEFI. Firmware, loads and, once it's finished initializing. The hardware it, goes and looks in two databases, one, is cleverly called dB I suspect. I've got far more chance of the people in this room defining, what that abbreviation means, than usual it. Literally is database they, could have caught it something a little bit more creative but it's a database of goodness what, it is is it's a secure. Variable, inside the UV for where that defines legitimate. Code signing certificates, so Microsoft's, code signing cert is in there some, of the Linux variations, SUSE and rel and all those are in there then. It's got another one called DB x which is database, excluded, which is the blacklist if you like of things that you should never load and it, can be either a hash of an OS loader or a code, signing certificate, something that is allowed to boot the system so. As the system runs the you if, he does its job it initializes or all that hardware and it then goes to the disk that contains the OS loader it, reads the OS loader then it compares the code signing signature, and the hash to, the DB variable, as long as it finds a match then so far it's looking good it then goes and does the same thing in the DB X to make sure it didn't find it there as well if it found it in both it will refuse to boot and you'll get an error if it, found it in neither it, will refuse to boot and you'll get an error if it found it in DB or the system will boot make.
Sense This. Makes it very difficult to, insert, root kits now because even. As people, in the product group Jakob, can't get hold of the code signing surface equal any more than I can get hold of the code signing cert for the Windows server operating system, we, have operations, and practices, that prevent employees from doing, that that's, all through automation it's very very difficult to subvert that process, there are far too many queues, and monitors, and physical processes in place to, stop that from happening so given that if you fee is trustworthy, which we have to believe it to be there's not much we can do to say that it is or it isn't we're. Working on technologies, to make that the case but we kind of have to trust the hardware we kind of have to trust the TPM so, you feel odes it, verifies, the OS loader the OS load of runs and the process, of booting the PC has started, guess. What the first binary, knows it. Knows the code signing certificate, of the second. So. When, the first binary is loaded we, start measuring things, we. Measure the first and then the second the first new the signature of the second and would refuse to hand off to the second binary if the binaries, signature. Had been tampered with makes. Sense so there's literally a chain here so, binary one which started from euphy knows, what binary two should look like and binary. Two knows what binary three should look like so there's our chain in the OS in addition. We also measure, the binaries by taking hache so, here we go with some TPM. Terminology, we take the binary we hash it we, store it into a register in the TPM. Binary. One looks at binary - binary - looks good hand control, - binary - now. We hash, binary, - and we, get a fixed size result again we. Look at the hash that we just put in the PCR we, concatenate, those two together so now we've got a double length hash we. Hash it again and put, it in the PCR, now, we go to binary 3 what do you think happens now we, repeat this ad nauseum, right the way until the entire OS is booted. It's. Not far off but it's not quite the same as blockchain cuz it's not as predictable but and you could obviously implement, something in there but you, wouldn't be able to detect it retroactively, Li it would really fail, but. Yeah it's somewhat, like a blockchain these are called TPM measurements, TPM. Is work by sealing secrets, to a set of measurements, so once the OS is up and running imagine it was BitLocker the, file system encryption in Windows the BitLocker, full volume encryption, key would be sealed to, a set of PCRs, that took certain measurements, in a certain way and the. Only time the TPM will ever release that key is if those measurements, are exactly, the same this, is how TPMS, work we. Do all of that in a hosts guardian service so when that sequel machine comes up and it's doing all of the boot paths for Windows and the Enclave and everything else that you've blessed it's, generating, a file called the TCG, log the, trustworthy, computing group log file at which, point that. Is what we need to see how the Machine booted and whether it's healthy, so sequel, machine boots up loads the UEFI, firmware, loads control, to the operating system does the building does the PCR stuff generates a TCG, log sends. It to the hosts Guardian service host, Guardian service compares it to a whitelist does this match if it. Does yes, then, it's all goodness we think but, somebody could have lied what if they recorded, the TCG, log off of the wire and then just threw it at me and it was nothing to do with what they did so, what the host Guardian service does is it runs through all of those operations, again calculates. What the values in the PC are on the TPM should be reaches, back into the sequel host compares. The values in the PCR compares, them to what it just computed, and says, if they match, I now, know who you are I know you told me what you and I can now with cryptographic certainty. State you actually did what you did last. But not least it looks for code integrity, policies okay. That's, what we're doing all of that stuff happens every single time a sequel, host needs, to get sufficient health, information, back from a trustworthy hosts Guardian service so that it can sign an enclave, report and have a client, be happy to talk to it and send, keys over to it, that. Post that process happens in less. Than a millisecond. Sounds. Complex but it's a PC they're pretty powerful these days so.
We, Have a variety of different attestation, modes that you can use the. Attestation mode, I just described is the one at the bottom, the. One with a nice big checkmark, next to it that's, the one that we recommend for production, environments, the top one active, directory attestation is being deprecated, as, in. We don't want to keep that around it's too complicated we've replaced it with something simpler, host. Key so the only two choices should really be should, I use host key or should I use TPM, if you're building a lab and you just want to see what sequel always encrypted with enclaves performance, is like use, host key mode to. Attest the host you literally go to the host run one command let ship, a key up to the host Guardian service and run one other command late' it's about three Commandments in total and now the machine is blessed to. Do it with TPM, you have to get the ek pub you have to get the TCG log you have to configure the policies, all of these different things that's the work that you put into production environments, long term but if you just want to see what sequel looks like when it's running with enclaves it. Doesn't make any difference how it was attested the performance, and the characteristics to say the same the only thing you lose by using host key mode is any guarantee. Of trustworthiness, in the host go, ahead. S. Jackson. Are somewhat unrelated there two security technologies, TPMS. Are simply used to measure things whereas SGX is like our VBS Enclave but done in hardware instead, of done in software. Question. There is do I have to have SGX as well as a TPM you do not know if, you, want you going forward which I'm not sure when sequel, are going to release that Jakob would know but there is going to be a sequel, enclave version of this as well it. Will function with that going forward right now VBS, enclaves, is available, on any host that meets the requirement, I just gave you which is pretty much any new, host you buy from anywhere even your laptops would meet this bar, okay. So use the host key mode if you just want to try sequel. Always encrypted with enclaves because, it doesn't affect anything to do with the performance all it is is about the trustworthiness, of the device use. The TPM mode when you want to do long term production, so, I give you a little bit of a breakdown here in terms of how each of them verifies, whether or not the machine is healthy and you'll notice that only the bottom one really makes an assertion of health the. Rest make an assertion of identity, I know. Who the sequel host is because he's got the private key I know who the sequel host is because he's domain joined and he's got this group. That's. All we're doing with the top two so. They are more about, recognizing. Somebody with some kind of cryptographic identity. But they are not strong enough because they don't measure the health of a host and if you're going to be feeding keys into an enclave to decrypt very sensitive, data you need to recognize the health of a host so. I would, urge that each of you take a look through these when you're building your proof of concept, to make your choice but, I will strongly, recommend, your best practice for any production, should be to ignore host, key ignore, ad that's being deprecated it would be a bad idea and use, TPM, trusted, only you, can see here we talk about how measured boot is required that was the TPM process I just described code, integrity enforcement, and that's kind of optional, you don't need to do that with a sequel host it's far more important, on hyper-v, and then platform, identity verification was, the part where we extract the endorsement, key from a TPM and use it as an identity. So. Last, part for me is let's, walk where, Jakob, will take on the role of the sequel client the driver and the sequel server and I'll take on the role of being the host guardian service and we will manually act out on stage looking like a pair of idiots exactly. How this flow runs right. All. Right so actually, I'd be playing collectively, the role of the, client, and sequel server okay so on the client side the, first thing that happens the application, sends the query right and the client.
Driver Intercept, it as. You saw in the previous animation so. The first thing the client driver, will do after that after, getting the application query. And, remember. This is the always encrypted, scenario. Right so the first thing that will happen is the same call. To. Discover. The metadata, about, which. Parameters, needs to be need to be encrypted and so on but now in sequel, server, 2019. We kind of overload, this. Interaction. We. Add a new purpose, to it right, so. This, this, call as P describe parameter, encryption, store procedure, invocation. It, it, also means. The. Asked to sequel server give, me a proof that the Enclave, you contain, is, trustworthy. That I can trust it's Enclave that I can safely share. The. Keys and use. This Enclave to perform. Computations. On my sensitive, data right, so. After that what I would do as a sequel, server, instance. I would, call Dean and, the. Host, Guardian service, to. Request. A. Cost. Health certificate. Right so, then what what is happening exactly in this stage so, that is again then what we come back down to the attestation mode the, mode is what controls what happens next if, you do host key attestation because you want to try this in a lab and see what the performance characteristics are, relative to none, encrypted, or the previous versions have always encrypted then, I would recommend you simply use the host key it will literally, take you about two minutes per sequel host to set it up it's that simple, if. However you want to see what the characteristics, are like when you're going through the real production, environment, which obviously you would tend to do in a lab before you truly rolled it out that's. Where this dance, that you see here would be give, me a health certificate now I won't give you a health certificate tell me who you are I am this EK pub look it up in my database yes I recognise, it generate. A symmetric, key encrypt, it with the public, send it back to sequel host sequel. Host passes, it back down into VBS, uses, the TPM, to decrypt it it's. Now got a symmetric key we've got a shared key now at, which point I'm gonna ask it give me your TCG, log it will then encrypt, the TCG, log and all that good stuff send it back over to me I decrypt. It compare it to the whitelist yet. You look good now, I run through that TCG, log recompute. What the values should look like in his TPM, reach, back over that connection, remotely. Into his TPM, using a protocol we invented called our TPM. Remote, TPM Cleverley we, reach back in validate. That the PTR measurements, look exactly the same as what we've computed and if they do job. Done health. Certificate, we. Throw back a health certificate that contains, a public, signing, key that. Was born on the machine inside our VBS, Enclave it was born there we send that back inside, the health certificate, and Jakob now has exactly, what he needs to proceed right so the sequel got the health, certificate. At this point which, was signed by AGA GS, was Guardian service the next thing it does it, calls. A local Windows, API to. Get what, is called an enclave report, and an enclave report, contains bunch of information about the Enclave, itself, and what's in it, what, is the DLL, or code, that is running inside the Enclave, and now this information is, provided. Back, to. Sequel client as a proof so, what. Follows is. Clients. Verification. Of that proof so, the first thing that client would do it would reach out to host guardian service and this is why we specified, this URL now, in the connection string, and when we interact, with.
With The database, in SSMS, this. Is the endpoint of the auto station service, that the client driver uses, to, get the public key of a GS and it uses them this public key to verify the. Cost health, certificate. So I could interject there as well what, that's doing is talking to an endpoint that existed, way before sequel, came and made this asker bus this is called the metadata endpoint, it's even how hyper-v, determines, trust in a house Guardian service you have to say at some point a human being trusts that machine you then go to an endpoint which doesn't require any authentication as. Long as you can reach it you can get it and it will send you back an XML, document which, is the metadata that describes the. Keying material that, this guy is using all, that's happening here is he's reusing. The same code paths we used in hyper-v, to go and get the metadata that describes a, trustworthy hds, so. At this point assuming. That we have used a TPM, mode right the, client, knows that the machine is is, healthy, and has booted properly, and most importantly, the hypervisor, which is the entity that provides the, isolation, and guarantees, the security. Of the Enclave is healthy, and secure and hasn't been tampered with the, next the, next step is, the. Client driver. Verifies. The, the. Enclave. Report, was actually signed, by this cost, and then, it, digs. In into, the Enclave report, and and verifies, the signature, a specific. Signature. Of the sequel dll library, that, implements cryptographic operations and. Operations, on on sensitive, data like. Range and so on, this. Library has a specific, signature which, the, client driver knows and compares, verifies, that that's what is running inside the Enclave, at at the end it also verifies, that the ante, by any chance is, not running with what, is called a debug mode so. You could run a VBS, Enclave in the debug mode when, we have. Developed, when we were developing, this. Feature our developers, use that a lot that's. Not what you want in production, because in the debug mode anybody. Can actually see the Enclave memory. That's. Only used for development, purposes so, we want to make sure the Enclave is not running in the debug mode so this is all kinds of checks and the verifications. We do to, establish. This, trust between the client server. Between. The client application the, client driver and the, server side arm clip that is supposed to be this trusted. Representative. Trusted extension, of the, client, of the, on the server side right the, main key, takeaways, from what. What, we, explained. The regarding, attestation, the, to auto station Markovski. Authorization, TPM attestation, used the first one. To get started with the feature there is extensive, documentation, I will point you in a moment as Dean said it's fairly easy you can set it up in a few minutes, TPM, attestation is a, little bit more time so yeah. Maybe not so easy but, still they're, reasonable. Well once you've done it the point being I think it is it's complex cryptography, does get complex but, you do it once right, once the host is up and running I would, say it's probably arguably worse for hyper-v fabrics, because they probably stand up and take down virtualization. How it's far more frequently, than you stand up and replace sequel, hosts because, they want them faster, than moving stuff around in your, model it's very much make it work make it work once and I'm kind of done yeah, go ahead sir. So. The question there is if I installed something on the host do I have to recreate the signature the way that we measure things is often done with code signing certificates, rather, than the hash of the binary itself because if we hash the binary a single, patch from even Microsoft will cause the hash to change so, we look at code signing certificates, for most for the most part such that patching won't do it if you, added a tool an admin, tool that, really depends, whether or not you're enforcing code integrity, policies code integrity policies permits certain things to run and in the hypervisor, will block anything else, Jakub, and I've had this conversation ad, nauseam now and for, sequel DBAs the, hypervisor, enforced code integrity, policy he, and I eventually agreed, is nothing.
So. You don't enforce anything whatsoever, because, the DBAs tools tend to be fairly. Frequently, changing, and there isn't anything that we can see in terms of an attack vector that, could be used anyway so, for, your binary that you're adding to the blocks if you patched something, or it was a third party say. Anti-malware, or something like
2018-10-30 18:17


