Achieving compliance by protecting and controlling your data with encryption in - BRK3115
How we can achieve compliance, by. Protecting, and controlling your data with. Encryption, in Microsoft, 365, and. That's. Gonna be kind of split into two parts and we're gonna share, the stage here a little bit I'll get, going and talk about asura Information protection and handoff. To Jaclyn she's going to talk about customer keys, all. Right let's get going. This. Is your digital estate today and why. Do we put this up at the first. Light for you to see because, this is the reality that you live with your. Data is spread everywhere, primarily. Because you have productivity. Needs that need to be satisfied you, use what is best for your users you, put data where it's required you, share with partners, you do what's required for your business but. Then you're, also required to be compliant, in this spread out world with, data spread everywhere and with regulation, coming in controlling, the data you. Need to do something about how. You deal with compliance, and how you deal with data and hopefully. This session is going to help you out with that. Now. Let's talk about why compliance, is challenging, well. We, all start, to, see now that there is a cost, to compliance, now. If you don't if. You're not compliant, there, is a monetary, aspect to, it that perhaps, wasn't there before it's, becoming, real to us and. Data. Is in some sense your biggest risk right, that's the place where all the regulation, is focused on this. Is where all the challenges, are. More. So now you, have regulators, coming, in with updates, on what they want to do it's a constantly, changing environment, the. Regulations. Are starting. To go from fuzzy to clear as we move on in time and we understand, what's going on in this space what. Is at risk and what is not both regulators and the, people, who are regulated, are coming, to a conclusion on where we need to go how, this needs to progress. But. Nevertheless the. End of the day what you really get to understand, is that the cost of compliance is increasing, and the, more you are not compliant. The, worse this is for you. Now. You move to the cloud we. We, talk about something called a shared responsibility model. When, you are completely, on premises, all, the responsibilities, up and down the stack completely.
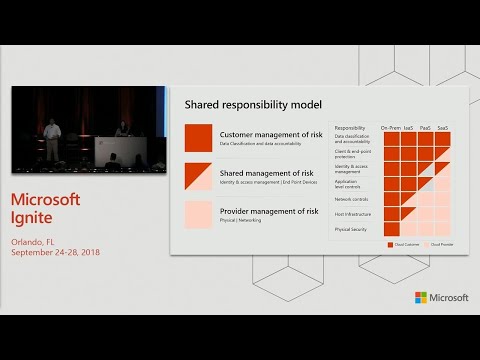
Yours, But. As you, move to the cloud some of this responsibility, gets, shared with, your cloud provider and, depending. How far you go whether it's ayahs pass or SAS the. Amount of responsibility changes. Nevertheless. It's, never, zero for you and in, this session we are gonna talk about some of those non zero responsibilities. That you have and we, will see how that works out and what, solutions we have to, help you in that space. Let's. Take a deeper dive and see what that split means if. You. Look at the various aspects, to it we kind of summarized, it into access. To production environment, protecting, your data and personal control now. We. Talked about shared responsibility which. Means there is some of this on your side and some, of this on our side and this, is where we get into what, do we provide to you to, help you end to end. This. Session is going to be focused on how you protect, data some. Of these capabilities, that you see are provided. By the cloud provider which is us and some. Of these things you have to put on top yourself depending. On your compliance, needs your, regulations. That apply, to you and what, is the best solution for your, your. Environment, and for your organization. What. Is really clear at the end of the day however is that, when. It comes to your side of the shared responsibility. Encryption. Is the way to go and, encryption. Helps, you protect your data in, ways that. Help. You out in terms of compliance and keep. Your data safe, now. We. Need to provide you solutions, on how this encryption, will work for you and that's what we are going to talk about in the next slide. Let's. Spend two minutes on this and understand, what is going on. Encryption. Options, in Microsoft 365, spread. From what is in transit, data, in transit to data at rest like, you have a variety of options that exist, each step of the way and each, layer of the data that is protected, so. In the transit, side you have TLS, which is of course over the network and on, the content, side you have office 365 message. Encryption and agile, information, protection to help you out a, data. At rest which is when your data is lying, in obviously, 65, or in the cloud you. Have BitLocker. At the lowest infrastructure, layer and you, have application. Level purity that is also provided, by a service, encryption. What. We are going to jump into a little bit today is the key management, options, that exist for you and we. Are going to focus on two aspects. For. The content, you have Microsoft managed Keys BY ok nsy ok and for. Service and encryption. You have the customer key and, why are we going to focus on this because the. Rest is already. Provided, by the platform there. Is sufficient documentation about, it as cloud. Providers, we talk about this all the time but. What we are here to talk about today is the, tools that you have additional. On top of all of this with. Responsibilities. That you have to protect the data what. Controls, do you get. Let's. Jump into data in transit, we. Are going to talk about agile information, protection and, office. 365 message. Encryption here. Summary. On how this actually helps. Now. What. You need to understand, is at the end of the day when, you need to protect your data, encryption. Needs to be persistent, in some sense wherever, your data goes encryption. Needs to follow which is how you show. Protection, show compliance. Now. How. Does a IP and ome help the. First thing is the. Access, to your encrypted document, is based on the user's identity which. Means you. Get to control who, it who gets access to the data and you get to limit, who gets access to the data first, step of compliance, it's, not open to the world, limited. Access from. Your decision, point right. Now. Once the data is encrypted you, share it out of the world share to your partners, who do have access it's. Not over there you, have a leash on that data, what. You can do is monitor, and, revoke that data if required which, means you can audit who, has had hacks access to the data you can monitor, and decide.
Who, Will have access to the data in that future and revoke. Data, access. To folks who had previously, access, to it which, means one time you grant access it's, not permanent you, have a continual. As access. Audit to it and you can change that level, whenever you feel like that. Is control, over your data that you previously never had a IP. Does, this for documents, and ome, does this for emails so, for all your unstructured, data you. Have a way now to both, encrypt, it let it out into the world but, also pull it back if required, and this, is huge, when you want to make sure that, when you're sharing sensitive data between you and your partners, that. Is not the source of where the data leaks. Now. When you do all of this it, becomes clear that encryption, is what, drives all of this in order to make, sure you can pull data, access, you're, actually, calling out the fact that encryption, is not going to happen so. The, decision, around keys, because. Keys. Is what drives the encryption, becomes, important, now. EAP and ome although. They act as the means to compliance, the access, to your keys is equal, to the access to your data that's what it fundamentally comes down to the, systems are in place you're. Going to protect your data but. Protecting, your data means keys keys. Become, important, now what you decide around keys is literally. What it means to be compliant, in some sense. Let's. Talk a bit about keys, in agile information, protection because that's what we are going to drill into today. There. Are three kinds of keys here the, first is a document. Specific, symmetric, key and this. Is important, because the. Key word here is document. Specific, for every, document that you encrypt this, is different. Which means there's only a, sense of, split. And there's, already a sense of isolation in, place in some sense. Now. This document, is encrypted and we mentioned that the person corruption is persistent, along. With the encryption we, send across a publishing, license that decides who has access, to this document. This. Publishing, license, is encrypted, with the public key. Of your tenant, now this is a tie back to your tenant now we went from a document, document specific, level to, a tenant. Specific, one so. The tie between your, document, and the tenant is this. Publishing, license, that gets encrypted with a tenant public key. When. You want to decrypt, a document, you. Need to first decrypt, the publishing license, which, will give you access to the document specific, key and then, the document, specific gives you use to actually decrypt, a document, so.
Again Routing, back to it all in, order to decrypt, your document, you, need a key that will actually decrypt, the publishing license, and that key. Is the, tenant private key so if. You want to start all the way from the beginning and bring it down to one single thing that you need to worry about is how do you control your tenant private key and like. All private, keys security, off the private key itself is super important, and that's, what we're going to spend the rest of our time talking about, the. Tenant private key is the, one single thing that will control, all of the data that you access, and what, happens, to it in some sense. There. Are three key options, in Azure information, protection. Microsoft. Managed keys bring. Your own key and hold, your own key we're, going to walk through one on each one of these in greater detail, and, you're going to understand, what it means to be compliant, with each one of these. Before. We jump into what the keys are this. Is a slide that I have found is super useful for most people to understand. Skews. Decide, what you can buy and the reality, is that not. Everyone, has the latest and greatest and the highest skew from. Microsoft, so, what, do you get with each one of the SKUs. What. What, is good is that the Microsoft, manage keys are, available to you across all the possible SKUs start, with office 365 III. You, get Microsoft, manage keys by default. Bring. Your own key as a capability. Is also available, in. 365. III or higher. But. You need an extra Azure subscription for. As a keyboard so you pay for keyboard separately, but you don't need to pay extra for connecting. The. Vault to your entire ecosystem. That deals with data, the. Last one is whole your own key when. We go through whole your own key you will understand, why it is so different from the others it. Requires. The highest Q, which, is EMS. A5m, 365. A5 or a IPP. - once. You once we go through this you will understand why it's kept separately why it is higher but. The other two encryption, options, are available to, you from the lowest possible SKU, o-o. 365. III, and higher and there's, a reason for this the reason is we want you to be compliant, we want, you to use all the options possible. And make, you decide, what is right for your business. Nothing. Holding back in that sense. Let's. Talk about Microsoft managed Keys, very quickly, what. Are Microsoft managed Keys when. The tenant private key is stored and managed, by Asha information, protection. That. Is us Microsoft, and this. Type of key this type of scenario is, then, referred to as the Microsoft managed key we. Manage your key and. Why. Is this, why. Is this important, to you why should you care for most. Organizations, this. Is all that is required it's sufficient. We. Provide, you the means to, encrypt, your data and, we. Keep it simple we, take care of the security in some sense and this. Is where that shared responsibility model. Comes in we. Take care of taking. Of. Keeping, the key secure so your responsibilities. Of the key also comes down as long. As you use the key, within the right, set of parameters. And our environment, you're good and, this. Makes it super simple to manage there is nothing additional that, you need to do it, just comes with your tenant it comes with your subscription, and it's. Readily, available if, you have an office 365 subscription attached, to your tenant. It. Is what, most customers, do today and, it. Is the reality that we take care of that responsibility, and it's, good with most people but.
We, Head into a zone where. Compliance, does, not necessarily, depend, on what, we think is important, it's what you think is important, and this is where bring your own key comes in. Now. When you use as your key vault to. Import, or generate, your key and you. Keep your key in like hardware, security modules. This. Scenario. Is called, bring, your own key. Now. This is important, what, you're essentially, doing is, moving. Out the key management, responsibilities. To. Azure key vault. Why. Is this so important, why is this different from Microsoft, manage keys. Because. With B Y ok you can show better key control. This. Means the end-to-end operations, around the key importing. Your key seeing. Actions, that and transactions, that happen against your key turning. Off access, to your key full. Control, of what's happening, there is. Under. Your control now when you use Azure keyboard, and, this. Helps, you meet certain compliance, requirements. Where, the compliance, officer or, the regulator, says that, you must show possession, of the key you, must show end-to-end, control, of the key and the, way to show end-to-end control is this, as. Your key vault provides you all the api's, to. Do end-to-end, crud, create, read update delete all. Of it so. That difference. Is really. What matters to certain organizations, and, eventually. Certain organizations, also, have policies. Historical. That they carry forward. They. Already have HSM and we say no you must, use the key that we have, generated. On premises that's, the one that we must continue to use in the cloud we, have certain policies on how we roll the key every. Six months every one year all those. Complex, requirements, around key management, can, be satisfied. With as your key vault and that, is the reason you pick me why okay, so. The reason to pick B why okay fundamentally, is compliance. Compliance compliance, that's. What this session is about and, I. Think, when you walk away from the session and you decide which key option. You want to pick I believe. That B Y okay is the right one for certain, organizations, that, require, these compliance, focused, audit. Related requirements. Now. We, talked about Microsoft, manage keys we talked about B why okay what. We haven't talked about is the impact on the product is. The product going, to behave differently, if you pick one option over the other do you lose. Functionality. And the. Answer is no. The. Way that the entire architecture. Works is that, you connect your key vault to Azure information, protection, that's. It it's it's, one change in the backend that you need to make you. Originally, used Microsoft manage, keys that's what was used by default you. Just switch, that over to a key vault that's, all you had to do your. Interfaces. From, either on-premises. Or from, the cloud will. Work exactly in, the same way, B. Y okay is seamless, which means if you want a higher level of compliance you, don't give up any capabilities, you don't give up any features, what, you do get is a higher level of compliance. So. This is this. Is essential, to, to ensure that you pick the right option, like. One key takeaway here is if you want B Y okay don't. Hesitate everything. Is seamless the capabilities. Just work. Some. Important, points to note when you're using B Y okay I use. A vault, that is different, from what. You use with the customer key and there. Are reasons, for this both performance, and latency, and the number of transactions. They're, slightly different in the way we use Azure key vault and how we interact with it so, the, characteristics. Of the workloads, are different use, different vaults, and. Jaclyn, will talk about the requirements of, her key vault related. Aspects. In the in her session or her side of the session now. What. You also need to make sure is that you put your vault, as close. To your tenant as possible, again for performance, and latency reasons. All. Of this is documented, in, the URL. That is called out there so. Everything. Is publicly, available all the guidance, that you require, to implement. Be by ok with. Azure information. Protection and office. 365 message. Encryption right. There. The. Other thing I do want to call out is that this session has been done before and there's, an existing, video that exists, with, an end-to-end demo on how to configure key. Volt with Azure information, protection the, PowerShell that's required the UI that's required, what, happens, when it works what happens on it when, you encounter, errors in configuring, all of that how to deal with actual, configuration, has.
Already, Been recorded and, it's, available to you right now so you, can start with understanding what, be why ok is what. Are the constraints, that you need to work against in terms of location of the vault and where. You keep your key and finally. You can walk through a video and finally, configure, your vault and you're done it's, super simple. Let's. Talk a bit about whole your own key, now. Hold your own key is unique. And different in its in, its own way and this, will require some discussion. When. You use an isolated. Ad RMS instance, that's, deployed, on-premises. With. A private, key that is separate, from what you use in the cloud. Then. This scenario, is called holder on key, when. I kind of walk through this a little bit more. You. Have now two, private, keys one, in the cloud. One on premises and isolated. The. Trigger for this is a label, you choose between a label, in Azure information, protection and it decides which. Key to use. The. Ad RMS, instance, on premises, is the one that holds your. Isolated. Key and. Isolation. Here is super, important, because. Isolation. Means, you have certain, kinds, of content that, can never ever see the cloud. You. Can't use hy okay for everything, because. Hy. Okay causes, opaqueness, to data hy. Okay causes, the Microsoft, cloud not, to be aware of what, is there inside the file or inside the email and this, has implications. But. This, is required, for certain industries this, is required for, certain organizations where. Having. The key in the cloud and showing possession, and maintaining. Those certain compliance, requirements, not enough there are more there. Are others that B yok does not satisfy and. More importantly, you have data, that you. Absolutely, cannot, take outside, your premises that. That. Data is so, sensitive, and so secret, then, it has to be encrypted, at rest even when it is within your organization, so. Keeping. Data encrypted. At rest within. Your walled. Premises. That is. The reason to use hy okay. That. Is not the use case for most customers. 90%. Of our customers will be happy with microsoft manage keys like. Up to eight eight. Nine percent, will be happy with B Y okay and the. Last one two percent is really who will require H Y okay. This. Is really what it is coming down to. There. Is very very little, very. Little that, hy okay actually will cover, so. The. Thing that we tell our customers is think. Twice think. Thrice and think. Ten times before you deploy a sh Y okay. Exists as an option for you but, do not take it lightly because it has severe implications for, the, environment. That you work in but. The good news in one sense is that B yok and hy okay are not mutually exclusive which, means you don't have to choose which, means you can start with a higher level of compliance with B Y okay and if your organization really. Needs it move up to X Y okay. Now. Let's. Talk about what, H yok provides and by. Design what, you will not get with it. Because. You encrypt, your data with, a key that's, on premises, isolated. And not visible to the Microsoft, cloud it. Means that data that's encrypted by it is going to be opaque you're going to get no indexing, no, search or any, other type of reasoning.
Over That data so. All the magic, of office 365, is essentially, lost if you use hy okay for your files, you. Want that for certain kinds of data and that's okay you don't, want that for all your data because your users are going to complain, so. You choose you, pick data that, you need to enter it with hy okay pretty, much everything else B Y okay is good enough. Data. Must remain in encrypted, at all times, inaccessible. To even Microsoft, in some sense. And. When I say Microsoft I don't mean Microsoft people I mean the services, that run in Microsoft, we look, into, that data we. Do things with that data we. Look at male headers we look at male content, we apply mail flow rules that go out right. Now if the, mail flow rule can't run because it can't inspect the data it. Kind of defeats the purpose of having a mail flow rule in exchange online in the first place so. All. These. Things that we provide in the Microsoft, services, the. Actions, that we can take on your data depend, on us being. Able to look at your data hy. Okay turns it into a blob. Encrypted. Blob that we just can't read just can't see into that. Has implications right. External. Sharing, this is huge. External, sharing is super, hard with hy okay. The. Way that it works because you have an isolated on-premises. Ad RMS instance. It. Becomes really really hard. Now. What, this means is, that. If, you do. Require. External sharing you work with customers you work with partners, you want to share data remember the world that we lived in where data, spread out and you're talking to each other that wonderful, productive world that's, dead, with, hy okay and that's. By design. Because. We want are really, really secure documents, to remain really really, secure and not, free floating around in the world with everyone's, access, to it so for. The kind of data that you want lock down external. Sharing wasn't, a requirement, to begin with if you, need external sharing on data. You. May have to rethink why it was why. It needed X Y okay encryption, to begin with so. Consider. What your data really is if. You read it lock down use X Y okay but. If you want it locked down why do you need external sharing so it, kind of works in parallel. Sorry. But. The most important, thing that X Y okay kind of provides. The. Kind of one, step up from B. Y okay is that it shows physical. Access, to your key now. This, is like a historical. Requirement, in some sense where. Physical, requirement, you can actually go to the hsm show the keys that plug it out and the. World kind of comes to a standstill, that. Has been the, requirement, certain organizations. Buy, policies, that have evolved, over time we. Haven't yet found too many regulations, that, enforce this but. Okay, historical, policies, require you to do it within your organization. This, is how you do it. All. Right. I'm kind of done and I'm. Heading towards. Handing. This off to. Jacqueline. For data at rest. If. There are any questions about this we are there at the end we'll answer them thank, you.
Everyone. So. Data. Encryption at rest so. Data encryption, at, rest means. That. When we actually write, that data down on to the disk, so anything that reads that data back up off the disk it's decrypted, from that feature perspective. So, we have two features in office, 365 that. Are data, encryption at rest features, so the first one is BitLocker. So. What is BitLocker. It. Is. Data. At rest at the disk player so. What that means if is if, someone was able to steal, a date a disk that was BitLocker, and put it into another machine they'd be unable to see the data that's on that disk, right. Because, they would have not have access to, the BitLocker keys. It's. Integrated. With the operating, system so, with. Windows machines, you BitLocker it through through Windows and use the the, chip that's on the machine and it. Prevents data compromised from. Physical, theft. And, as. I said it uses the TPM chip on the machine so you usually have to have a TPM, on the machine that you're actually BitLocker, in the disks for in order for that to work and, it. Uses AES, 256. Keys. So. We have that on in the data center in office 365, on the, backend machines. So for Exchange SharePoint onedrive. For business and, Skype for business for the data that's stored in a, mailbox. So. What is the value proposition of, BitLocker. Data. Lost. Or stolen a distance is inaccessible, so like I said if you were able to take a disk out of a data center and put it into another machine it would be inaccessible, to you, it. Also enhances, the file and. System, protections, so, as, a person. That has BitLocker, on my machine. And unable, to get to anything on that just be it like the operating, system or anything else on on that particular desk. It. Also renders, the disk. Data. When. You decommission, or recycle, that particular. Disk it renders it all inaccessible. So, from, the moment that you pull that just out of the machine when it's no longer able to access those, BitLocker, Keys it is, inaccessible. From. That, particular, feature perspective, meaning that nothing on that disk is readable to anybody else. So. The next layer of encryption, is something that we are working on, and have released for customer key in, the last ignite, in 2017. And. This is service encryption. So. What is service encryption, it's another. Data. At rest feature, but we're doing this at the application. Layer so. Instead, of it just being disk layer protection, we're, doing this at the application, layer so for example in exchange, for doing this as we write the data down into the database, so, from. The future perspective, of somebody. That was able, to log. On to the machine and copy, a file, off that. Particular file will be unreadable, to them because we are encrypting, it as we're writing it down onto the disk inside, of that database so. It separates, the Windows, administrator, from, the data. It's. An additional, protection, against, physical, data theft in that again, even, if that particular just did not have BitLocker on it and not just was stolen out of the data center and put on to another machine you'd be unable to read the data because the data inside. Of that particular database is encrypted. It. Also provides, the customer the option to. Have. Microsoft. Managed, or customer. Managed keys, so. In SharePoint, today we already have all of the data encrypted, at rest with, Microsoft, own keys and like I said we release the customer, key feature last, year at ignite in 2017. So the customer does have the ability to own, their own key root keys to their data in, exchange. Online we did it a little differently we did not already have all of the encrypted. With, microsoft own keys so we started with the customer. Key version so you are able to purchase. The feature that is called customer, key and encrypt. All of the data at rest, in office, 365 with, that in exchange. And in SharePoint Online the. Customer. Managed. Keys like I said was released, last year the, Microsoft, own keys in exchange online will, be starting, to roll out to the environment, in January, of, 2019. So. What is it service encryption with Microsoft ink owned keys, so Microsoft owns the route keys to the data so, be that sharepoint online onedrive. For business. Exchange. Online or, Skype for business and. We. Own the route keys and it's very, much the same in exchange, online as it is to customer, key the, architecture. Is the same so in exchange online we still store our keys and as your key vault I will be explaining that a little bit later and as, she said earlier there is a feature where you can bring your own keys from on-premise, this hsm and put, that into Azure key vault and use those keys if you wish you, can also create keys. And as your key ball. Office. 365, data, customer. Data that, is non encrypted with customer key will get the, Microsoft, own keys so in a, IP where.
An Ome, that ashish was showing earlier we, were talking about like if you don't own the, keys then Microsoft will own key so the data will still be encrypted no matter who owns the keys and, as. I said this is already on a SharePoint Online and will begin rolling this out to exchange online in January. Keys. Are stored in our key vault and the data encryption policies, for. The Microsoft, own keys in exchange, online will, be, created. Per forest so, in SharePoint, Online that's, a little different but in exchange online we will be creating data, encryption policies, I'll explain those in a little bit per. Forest in from, with the Microsoft own key version. Service. Encryption with customer, key so this is the one that's probably more interesting, to everybody helps. Meet the compliance, and regulatory Jemaine she was talking about earlier there, are a couple of countries in the world that have this actually written into law so, there's only two that we know about today and that's New Zealand, and Israel, the. Rest of the compliance. Requirements. Are a, lot of compliance, groups. Within customers. Today have interpreted, some kind of laws they have to own their own keys to their data. If they have their data in the cloud. We. Have not seen any other countries. Besides those to actually write it into law but, there are some that could be interpreted, that way and so, we do allow for this feature that we released last year, it. Is customer, controlled, keys it enables. A revocable. Data, destruction, so I'm gonna talk about our data deletion path so how, you get rid of or make that data crypto, deleted, when you exit the service or have a divestiture, at your company so, the feature was really, written for for. That case when you leave the service to make all of your data inaccessible. So, today when you sign, up for office 365 and you sign that that OST, those online, service, terms it does say in there that if you decide to exit, the service that your data is gone within 180, days this. Feature will actually make you have, the ability to do that much sooner.
This. Feature was actually independently, audited so, we have gone through sock audits both for exchange online and sharepoint online versions, of this feature so you can read those online we do have those all published, share, points just went through this year so theirs is not published, yet but will be in the next couple of months exchange. Online went through our sock audit last year and it will and it's already published if you'd like to read that so we really do what we say we're gonna do we, really do, encrypt. Your data at rest and we really do allow you to go down the state of deletion path and make your data inaccessible. In. Exchange online we have flexibility, and data encryption policies so like I was saying before there is these things called data encryption policies, what, that means is you can have a set, of route keys that you tie, to your, data and how we do that in exchange online is you take a, set. Of route keys you create this data encryption policy thing and then you assign, the policy, to the mailboxes, that you wish them, to. Encrypt. So. Those mailboxes, that are assigned to that data encryption policy that's pointing to these particular route keys are encrypted. With that data. It. Also allows, for an. Experience, whilst like, the full feature, rich experience, of office 365, while. You have this data encrypted at rest so. We in the past we've seen a lot of customers, do something like Ashish were saying before which is bring, the data in already encrypted, right. Then, we can't reason, over that data and therefore the our feature set is much less because we cannot get to that data so we can't content indexed we can't search. There's. A lot of things that we can't do do, any analytics. Against that data because it's it's opaque, to us so, with this particular feature, what we're doing is this. Is a particular. Or, this is the regular, exchange, online. Access data, flow so, there's you see a bunch of clients at the top and then there's some internal, workings of exchange but, where I want you to look at is down here, at this very, low level, at the store level is where we actually encrypt the data as we're, writing it to disk with, a process. What we call jet so. With, those particular databases. It's written down on to the disk encrypted, so, again anything that reads, that data up off of the disk is decrypted from our feature perspective. Of course, you can do ome, AIP, a TP anything, against, that particular data once it's read up off the disk to be encrypted from those feature perspectives. But. From our particular features perspective, as soon, as it's read up off the disk right. It is, decrypted, so. That means that again. Back to the, feature sets of office 365 the anything that's able to read that data up off the disk the feature will work for him so. Let's, talk a little bit bit, about how we set, this up with a dirty vault so, Ashish, was talking about his BYO k and hy ok feature. Set with. ATP, and ome so, they. Also use, Azure key vault as, their key store but. We use it a little bit differently, in that we require, many. When things in order to set this up so with. With those feature sets there are a small, subset, of the data that is actually encrypted, so if you lose the keys to those particular messages. That won't work right but, with SharePoint, Online and Exchange Online you, are out for, your whole workload, so, for example for exchange online if you were to mismanage, or I don't know get hacked and maybe you Brandt somewhere with your keys it, is possible, that you could lose all of your, exchange. Online or SharePoint Online data, right, and with. Our particular feature sets you would not even be able to log into the environment so for exchange, online you can't even log into your mailbox you can't send receive mail so, even though it is data at rest that is encrypted. We, do have, the. Entire. Mailbox. Encrypted, in an exchange online so all the tables, and rows all of your metadata, so, if the keys are unavailable, to us you cannot even log into your mailbox. So. How we want you to have this set up so we want you to have to as your subscriptions, that. Are distinct. So not, the same as your subscription, that you have other things in like maybe your office 365 subscription, but. Two distinct, add your subscriptions, with only key vaults as resources, in them, we. Want you to place these subscriptions on this thing called we call the mandatory retention period, list so. When. You, are. Able to delete your subscription, all of the resources, that are under that particular subscription. Go, inaccessible, so.
We Don't want you to be able to delete your subscription, and therefore the keys underneath, them and make all your data go inaccessible. So. We have this thing that Asher. Actually, helped, us create with them that's, called this mandatory retention, period, so you cannot call in and immediately cancel, your subscription and, therefore all the data underneath it goes inaccessible. We. Also want you to assign distinct, administrators, to each subscription this, will become crystal. Clear as to why when. When I go down the data deletion path with you guys a little bit later but, I separate. Distinct, administrators, due to things like account compromised, so, if an account was compromised, and happened to have permissions, on both vaults somebody, might be able to either delete or take, possession. Of those keys and therefore. Your data right so we want to have two distinct, sets of administrators, on. Those, particular. Subscriptions. We. Also want, you to have HSM. Protected. Keys so in as your key vault you are able to create a software, backed key I want you to create a hardware. Security module. Backed key because. It's much more secure. We. Also want you to enable soft delete so, there's a new feature and as your key fob that came out I don't know about eight months nine months ago, where. You are able to turn. On soft Delete on your keyboard. And. Then if you delete a key within that key bolt you can reconstitute, it within about 90 days and if, you are able to be constituted in 90 days that key is still usable, the. Reason that we wanted to do that is there, are possible. Miss management's, of keys or again like we were talking about ransomware, where, somebody. Ransomware is you and you're unable to get access to those keys you want to be able to be able to reconstitute those, so that your data is not gone, from office 365. We. Want you also to ensure, that the subscriptions, and vaults have proper. Retention, retention, settings, before you actually create the keys within those faults so. The, mandatory retention, period is on right. And soft. Delete is on on that vault and on. The key you'll be able to see an attribute. And it. If it's set to this particular, value. Then, both, of those things are on in your subscription and on your vaults, we. Actually check for that so if you try to create a data encryption policy where the keys are not set to this particular, value it. Will. Fail because. We want to make sure that you're protecting, yourself as much as you can so, you don't make your data go inaccessible, to yourself, let's. Talk about the exchange, setup so, now you have two sets of administrators. One for each one of those as your subscriptions, now. You want, to have a different, distinct. Sharepoint. Online or, exchange online tenant. Administrator, for that data, you. Also want to choose compliance, groups so in exchange online like I said you can have multiple those, data encryption policies, and to, get those, mailboxes. Tied, to those particular root keys you assign a data encryption policy to a mailbox. Most. Customers want to create these. Compliance. Groups, either by geo. Or by. Let's. Say Department, so maybe you want your HR department to have a different, set of keys than your legal department maybe, you want North America, to be separate, than Europe. Or, maybe you want to do it by. Geo. And Department. Maybe your legal department in, Ireland, has a different set of keys in their legal department in Singapore, for example, in. Exchange online you're allowed to have up to 50, data encryption policies. In. SharePoint, Online that's a little bit different in SharePoint Online you can only have one data encryption policy, unless. You're a multi, geo customer, and. If, you if, you are a multi geo customer, you all are allowed to have one data, encryption policy per. Geo. So. How. That works for the exchange online administrator. Again a separate, person, and the people that administer, the subscriptions. They. Will create these data encryption policies, because they were given, the, URIs. Or the way, to get to those particular keys that we created an azure key Balt we. Create this data encryption policy within Exchange Online or SharePoint Online and then we assign, those, data encryption policies, to the data that you want to corrupt it with that.
We. Do have special. Licensing, requirements. For, this. For, the customer key version of this feature again. With Microsoft. Own keys you get that for free so all the data at rest, will be encrypted at the application, layer with. Microsoft, own keys but if you choose customer, key you do have a licensing, requirement, it is, 'if I've or the advanced compliance add-on and I, will add a note here that in, exchange online we check that at the mailbox layer. So. If a particular mailbox. Is not assigned, a proper license we will fail the assignment of the data encryption policy. So. There's, a lot of features that are in our compliance, advanced, compliance, add-on, that, are kind of like a gentlemen's, agreement as to we say you have to have this licensed, and in order to use this particular feature that you should have all these mailboxes licensed, and. For, customer key for exchange online we have codified, it so it is a requirement. That you, have those particular mailboxes. Licensed, properly, I, get. A lot of questions about this availability. Key thing so let me let me address this so. It's. A value add to our customers, so they. Can recover. From, a data loss scenario so. As I said before we, have to as your key vault keys per data encryption policy we also have this thing called an availability, key. We. Use the availability, key, to be a third, root key that can wrap this data encryption policy key so any one of the three keys that is available to us we can use to unwrap, the data encryption policy key, and therefore, unwrap. The mailbox key which, locks. The data for us. So. It allows, for high availability in. Exchange online, so. Let's say, you. Are attempting. To go down the day deletion, path you both of your as your key vault keys are out, but then your CEO won't. Sign the document, that allows you to completely, go down the data deletion path right so. I'm gonna talk about a little bit more later, how four people have to collude in order for your data to go inaccessible but, in this case if. Both as your key, vault keys are unavailable to. Office. 365 and. In, this particular example, I'm, using exchange, online I would then be unable to do things like decommission. A server because I can't move the mailbox because all of the metadata and rows, and tables of that mailbox are, encrypted, and so, I can't decom, a server I can't, do anything like content index or, deliver. Mail to a mailbox for example, right, so I need to be able to run the service. Even. When a jerkey vault keys are unavailable to me so unless this particular, data encryption policy has gone down the data deletion path this availability. He is available, to me.
It. Is controlled, by the customer, however like. I said we have this thing called the data path in the data deletion path we will delete the availability, key, it. Provides. Defense-in-depth. So. This particular key, is stored in a, key, vault. Structure, that we have created in office, 365, so it's stored on office, 365 back-end. Machines not an azure key vault so in case we had some kind of catastrophic loss. Of, connectivity. Between, the office 365 data center and the azure data center you would still have the ability to access, your data that's in your. Mailbox. So. What is the availability, key used for so, it's only ever used. If both, as your key vault keys are unavailable to, office 365, ok. So if either one of those azure key vault keys are available to us we. Use one of those two azure key Balki's we round robin to them and if one of them is unavailable to us we try the other one ok so, the availability key again is only used. When. Both, as your key phone keys are unavailable to, us. It. Is used in three cases, one. For transient, issues let's, say we have a networking, issue or, are, unable to get an OAuth token, to authenticate. Against a particular key. Vault, we. Will then fall. Back to the availability, key, to. Use in order to have, access to that mailbox, the. Second one is emergency. Restore of service so, as I said this is a value add to our customers, so if you are compromised, or your keys were mismanaged. And you, no longer have the ability to log into your mailbox you can call us and we can switch to using the availability, key, for your user set, so. What we do is we actually lock. The users out of their mailboxes. When. Both. As your key vault keys are unavailable to, the office or 65, service, so. Your user base will be unable to log in to office, 365, either. Be an exchange, online, or SharePoint online. So. You, can call. Us to make that changeover, we. Then of course will require that, you create, a new data encryption policy that. Have keys, that you own on it and switch all the mailboxes, to using that instead. And. Then the third thing is system, calls so I mentioned that we have to be able to do things like move a mailbox or content, index amount the mail in the mailbox or deliver. Mail to a mailbox, we. Have to be able to do those things in order for the service to run so, in the case where both. A jerky vault keys are unavailable to, the office 365 service and we need to do some kind of system call to the mailbox we will use the availability, key if it exists. All. Right so let's talk a little bit about this data purge path thing I was talking about before so, we. Have normal. Operations, of exchange. Online or SharePoint Online then. Somebody, decides, some, data owner decides, we need to get rid of this data so that'd be it for leaving, the office 365, service completely, or maybe you have a divestiture, at your company so you have a set of mailboxes that need to go down the state of deletion path. Ok. So the. Decision, is made I need, to divest, this, particular company, I have a hundred mailboxes. That I need to make inaccessible. So. There are several steps that need to happen and the, video is going to fill up really quick here guys so this is not an easy an easy thing to do so, as you can see with my key there, are multiple, people, that. Are involved, here and they should be all distinct. Individuals. And. These boxes are colored in with who and who needs to do what ok, so. Normal. Operations, somebody decides here we're having a divestiture. The. - Azure. Subscription. Owners, and. Again, those suits should be two distinct, different people or maybe groups of people where they don't overlap. Need. To make, the, keys. Unavailable. To office, 365, so. Usually that just means removing, permissions, from those keys ok. Then. The. Third person which, is the exchange online or SharePoint Online administrator. Needs, to make a change and set on that particular, data encryption policy that they were going down the data deletion path for an attribute. So, now we have three people that already have to collude in order to start going down this data deletion path thing the. To Azure subscription donors, and the. Exchange. Online or SharePoint, Online 10 administrator, that's three people I will. Say also that the exchange online our SharePoint Online 10 administrator, cannot, set this attribute, on a data encryption policy unless both of those advocate, vault keys are unavailable to the service. Once. That happens we do a bunch of stuff on the back end so, we check to see if the other as, your key vault key is available to us for example, we. Put. A message on your message, center for your tenant saying hey there's, something wrong with your data encryption policy please go fix it, and.
Then We also say. Make. Sure that if your key is available, your other key is available, to us we do, use it so we do allow the, mailbox to be decrypted and the users to log in. If. It is not if the second, as your key vault key is out then. We have a service outage for your users ok, your again like I said your users are locked out of the service, if both, as your key vault keys are unavailable to us but we do continue to use that availability, queue for system. Calls. Once. The service outage happens then we all get together we probably will. Contact. Your account team we, will talk to more people about who, and what and where we need to get into a room or into onto a call, and. We. Make, sure that you're continuing to have this outage, not make sure but you, will continue to have this outage, we. Get everybody together we. Talked to you about what, this means if you go down the state deletion path meaning that all of your data will go inaccessible. We. Make sure that your. Attribute. Is set on your data encryption policy that you really are meaning to go down this state of deletion path. And. Then if you, don't you, can restore, that at this point you can restore, service. But. If you want to continue going down the data deletion path we notify, your account team and we get somebody, to sponsor. Signing. An e document. That allows us to continue, down the data deletion path to, delete, that availability, key, and make, all of your data go inaccessible. So. That fourth person so you've got three people at the beginning the two other subscription, owners. The. Exchange. Online or SharePoint Online 10 administrator. And now this fourth person so when you signed up for the feature you. Said, there. Are these roles, that, can sign this II document, that can make my data go inaccessible. We. Usually put people. Usually put c-level, people on there, so. You have like. Your CEO for example or maybe your seaso is the one that can sign this document we. Do ask for that information up front so when you sign up for the feature you say who your data owners, are once. We receive that document, back and it's signed and that attribute. Is set in on, the data encryption policy then. We delete, the availability key all your, data goes inaccessible, at that point so. Again before. The, OST terms, your, online service, terms of a hundred and eighty days you can go down the state deletion path and make this data inaccessible. So. Red, box all died. This. Is it's. Also unrecoverable, at that point. So. Four people have to collude. The. Two admins. C-level. And. The availability key, is definitely, deleted in that in that particular process. How. Often does this happen so so far not. Yet. Right. Of. Course we've done our testing it works right, and we I. Said, we've been through that audit, right so we did go down it for that for the auditors, to.
Make Sure that they saw what we were doing and that the data was all inaccessible, once we got down the path and deleted, the availability key and all of that but. No. Customer, has asked us for this yet and again because this feature is for leaving, the office 365 service or, having a divestiture it probably happens pretty rarely at. Least we hope and it happens, pretty rarely we want people to stay and Jane's online and sharepoint online right question. Here. Yep. Okay. So the question is how. Granular. Can, we be if we want to do this data deletion path and, specifically. For a divestiture and in this case it. Can be at the mailbox layer, like. Single mailbox we, don't recommend that because we have these things we are calling compliance, groups right and we wanted these groups assigned to two, particular mailboxes, and you can only have 50 data encryption policies, right. But. I, if. You, wanted to you could create, a new data encryption policy move, that, particular. Mailbox, or 100 mailboxes, or however many you're divesting, to that, data encryption policy and take that data encryption policy down that path, that's, you so it's pretty granular and Exchange Online. Problem. With. SharePoint Online is it's all or nothing so a sharepoint online that's different we they, are investigating, on now how to do, that with, at the site collection layer but. But they're not there so, for. A sharepoint, online it, would be it's, an all-or-nothing it's, your, entire tenant oh unless, your multi geo and then you can have multi. Data encryption policies, but, for, most people it would be singular. It would be all or nothing for exchange, online though it's its mailbox layer, yeah. Question here. Can. A customer, do. A gdpr. Request, to. Delete all of this particular, data. Because. Gdpr, is user based right, it's off a particular, user I would say they, could, but. It would they would have to figure out which, data encryption policy to sign to which particular user, because. Gdpr is on a particular. Person, I. Can actually answer that. You. Wouldn't use this process to delete data for, gdpr. There. Are there. Are ways in office 365 that. Allow you to comply with gdpr without going down the path of purging. Your keys and could like that for admin scenario this is for something else altogether so. If you if you want to go down use. GDP, a request user asked to delete their data there is a different, path in office 365 to do that. Okay. Let. Me wrap it up and then we can open it up for questions for either one of our on features, I. Customer. Key features, set up maintenance. And the purge path are all complicated so, I know I just showed that that. Visio, diagram, of the off-boarding, scenario of that data deletion path the, sign up process is just as complicated so, you want to make sure that you again like issues were saying about his feature heavily, weigh the reasons that you want this and what the business specifications. Are for, signing, up for the feature best. Practices, should be followed so we cannot, enforce, for example you having two different sets of administrators. On those. Either. Subscriptions. But. We want you to ensure that you have enough of those people that have to collude in order for them to go down the data deletion path, so. You want you to follow all of the best practices, we only have some of them codified because there are only some that we in exchange online and SharePoint Online could do checks on, but. We do want you to follow the best practices so in our documentation. For setup for customer key we do have a lot of call-out, so there are a lot of notes a lot of things to think about a lot of little important. Things that you should read. Customer. Key gives, the customer the ability to know when their data is no longer accessible in office, 365, so. Again. OST, will say a hundred and eighty days but.
It Could be any time in, 180. Days with the particular customer key feature if you do decide to exit. The office 365 service as soon, as that document. Is returned, to office, 365. By. That data, owner and signed, we, will delete the availability, key we will be done with that particular, data so it will be crypto deleted at that point. And again in. Exchange. Online at licensing, is enforced, at the mailbox layer you want to be crystal clear about that because the other features in our particular add-on. Are, are not that, they're, not enforced. All. Right so on to, questions, do we have any more questions about either one of our feature. Sets. Okay. Yeah. So. The, question is is there separate licensing, for like. Customer, key and like a IP, and ome so, if it's if you do purchase 'if I've it, includes, both correct. But. I but. With like, the advanced compliance, add-on it includes mine but it doesn't include his for example right, so, we. Certain. Features aren't certain add-ons, in office. 365 and so. But. Like II five for example has nearly everything. That's. Right. The. Hy, okay capability, comes only in the. AIB, p2 or EMS, a 5sq. So. If you want, per. Feature plus my feature, you. Can buy, office. 365. Fi plus a IPP, - or the, encompassing. SKU, is called M 365, a5 it'll have everything. Any. Other questions. I, also. Before, we we. Finished I want to be crystal clear about the. Naming conventions, for these features so I know that that BY, okay hy okay has talked about with with, AIP and, ATP and ome, and. Customer. Key is talked about in office 365 so we do have different naming teams, and as in office 365 so, we name them different, things and. So. When we talk about the. BYO. Khy. Okay we're talking about mostly azure features, right and we're talking about something like customer, key we're talking about things in office 365 it's. Very confusing because our feature used to be called advanced encryption with Bui okay we. Then changed, it to a really, long name which was like mailbox. And file, level encryption with. Customer, own keys that's way too long, so. We now have changed it to service encryption with customer, key for my particular feature or shortened, to just customer, key so it's no longer referred, to anything with B Y okay because and it gets very confusing, between our features. Any. Other questions.
All. Right great thanks everybody. We're. Here to take an equal.
2018-10-09 07:42