Using Azure Confidential Computing for your security regulatory and compliance needs - BRK3295
Okay. We're closing the doors we're about to get started, thank, you everyone for joining us at, 4:00 p.m. on day one, the. Room is almost full I don't, think it's half full it's, great thank you. We're. Going to talk about as your confidential. Computing, so, the objective of this session is to educate. Everyone a bit about the computer. Stroke computing, initiative, and. Go will be deep, so. We'll have a few demos and we'll, go a bit deep on the. Technical side of confidential, computing. And. I would like to like. Organize, the session that way will will will, have a few slides to take you through presentation. Will cover some demos and, I think we'll do a bunch of Q&A a lot of Q&A at the end my. Name is Christophe Hrbek and I'm. With the azure compute team, based. In Redmond and, with. Me today, Jakob, and. Jakob, is one. Of our sequel experts so Jakob will cover a sequel. Always encrypted demo. And. Later Michael Glaros, will join us. To. Cover, another demo on the, blockchain. And the. What, we call like a confidential. Consortium, blockchain. The, challenge, is Michael is also, giving another presentation, at the same time and. We're. On and we walk a lot here right so. I, think his session. Is actually kind, of the other side of the of the convention, hall so, it's gonna be running fast so hopefully, makes it on time and. We'll. Need to give him a break if his penting for half of his demo. I'll. Grab this. And. Get. Us started so. When. It comes to data security in the cloud right I'm like data and code have talked about data and code specifically. Today, I. Think. The cloud is pretty safe and pretty secure, its most secure more, secure, than, most on, premise. Platforms, it's, still a big concern for everyone right, it's, still a big challenge what. Happens to the data what happens to the code when it's in the cloud who, has access to this and. Confidential. Computing is this initiative, that. We. Form to address these big issues I think. Number one issue is, what. If someone who's not supposed to have, administrative. Privilege, to your data. Or. Access to your code gets. This access, and does something with that data on that code that, it was not supposed to do with. Second. Scenario are people hacking. And. Today, because we encrypt. The data in, storage. Most. Of the hacking happens, when the. Data and the code is brought to memory and, people. Like snoop that data at that time and that's what makes this data a vulnerable, right, the.
Third Big threat or. Or concern, is like, these third, party accessing, data, without your. Consent, right and, we'll try to talk about these three. Today. In the presentation. What. A jerk official, computing, is it's all about how. Do we, guarantee. That the data is safe and, you. Have control with this data wherever. It is whatever. Happens, to this data in the cloud, so. You're, familiar with encryption. At rest in, storage data, is in, Azure it's encrypted in Azure. It's. True for most data signature. Today right, the. Data is also encrypted, in transit as, it. Moves either through, Azure. Properties, or from your on-premise. Data. Center into Azure right and there's like multiple ways today to. Protect that data in, transit. What. Do we do to, protect data and, it's as it being used by. The applications. That you run in, the cloud and. This. Is what confessional, computing is about is bringing. This, new how. Do we encrypt data in use so. The data is always encrypted, whether it's addressed in transit whether, it's being pooled and used by an application that. Data is encrypted at all times. And, there's two ways today to, technology, ways. To. Protect data and, encrypt, data in use it's. The. Technology we're going to be talking today about this trusted. Encryption, using. Technologies, like Intel SGX or. AM a morphic encryption, and I won't be talking about a morphic encryption, today. So. You know guys this. Exists, as well. So. Our vision for a confidential confidential. Cloud. Is. Really there right is, we. Want to have a, cloud. You want, you to consider Azure as a platform, where. The data you run in the platform, the, code you run in the platform, is a. Pack, to the platform, right. If that, really. You should not be you, should not be considering, whether as you can see the data in treasurer can, process the code or can, do. Something, with a code you should have all of that in your control. My. Voice sounds very robotic so are you guys like with the is. That okay with you you can hear me well okay. For me like it sounds super robotic, so apologize, for that but. Really is how do we give you full. Control, of, this, data and. So. That you consider the platform, as just a platform where you're going to run stuff right. So. Today, the presentation we're gonna pivot the presentation, across these six, six. Axes, I. Don't. Refer to. Confidential. Computing, as a, product, it's it's not really a product, it's. A series, of. Hardware. Implementations. Some software implementations. And, attestation. Right. So, from a hardware perspective. It's. What. Are the technology, what is a hardware technology we use to enable. That capability, to. Encrypt, data in use right. From. A software perspective how. Do we serve that capability to you in. A way you consume, already Azure today right, through, virtual. Machines. Through services, and. That this station is super important, because it's a station. Is. The service that we run on top of this so, if you're familiar if you're running. Security. Systems in your own unpermitted, Atta Center today, you probably run your own attestation, program, right all. The logs how people how. Services. Our applications, are accessing the data where. You capture that log is there a process that reviews this log and.
Give. You alerts give, you control give you hey, this is what's happening to my data as my data being tampered by someone, as my, data being accessed by someone and how. Can we build a process and a. Service, to. You as users, of that service, and Azure that. Includes that Microsoft, run as your run at the station and, when. You combine all of that together hardware. At. The station, and compute, then. You have what we call that as, your configuration, computing. Initiative. Right. We'll, be talking with Jakob. We'll be talking as well about what. Are the use cases what. Are the development experience. And how, we keep partnering, with. Intel. With arm, but. With also Microsoft, research to just continue, building the. Capability. To improve. The program. So. Why would you need. Confidential. Computing. For. Right, there's, a bunch of use cases a lot, of them are very specific. To your businesses, and, the. Way you operate your, your platform, today. Protect. Data is pretty obvious right there's there's data that is. Private, to you your customers, you. Want to protect that data whether. Your applications, are on-site or whether you are accessing a remote. Location and, how do you ensure that data is safe. That. Could be applicable to code as well. If. You are a business that. Has I'd, say a specific. Secret, than the way you do things right. Whether. It's an algorithm that is your proprietary. Information. Like. Some standards, of how you operate the data right not, only the data itself with the code you're going around and the data you, want that code that algorithm to. Be untempered right you want that code that code not to be accessible. By, anyone who wouldn't have wouldn't, have the right to see the code right. The. Trusted, there's, a trusted, network of nodes among, a set of interested, parties or how, do you centrally combine different data sources for better algorithmic. What. We can do with could financial computing, we, can use. This. Trusted, environment so. That different parties can bring their data or can bring their code, share. Information, together. Without. Any, of, these parties being able to access, code. Or data that is being brought by another party right, so an example here, would. Be like, we have some customers like big hospitals, right, they, want to put patient data, together. So. That they can build some. Intelligence, on how. Should it really improve their system should they improve their care but. That data is very, confidential. Right so as they bring data. So that they can build an algorithm and, understand. What what. Trend they can see in this data they, don't want other hospitals, we could contribute initiative. To see that patient data right so, they're all bringing data together they. They execute, they. Are GU rhythm on that tool in a trusted, and clave but. Then the data is not accessible, by any other party than that right. Do. I miss one yeah good you. Think you're good yeah keep, me honest. Right. So let's dive in I'll, start with hardware. Our. Service, as. Your credential, computing, today runs, on. What. We call a. Tee. A trusted. Environment or, an, N clave.
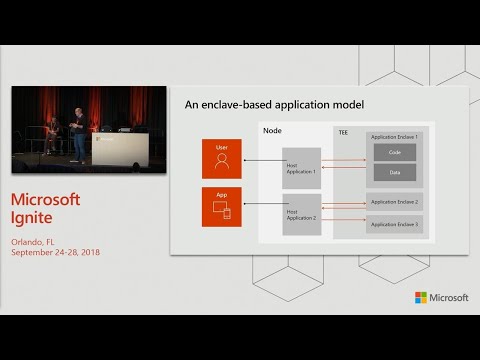
It's. The basically on the, chipset a, portion. Of memory, and, CPU. That. Is being reserved, for. Executing, these. Confidential. Computing. Operations. Right. It's. Sealed. Which. Means that once you have, code. And data within the in clave it's not accessible, by anything, outside. Of the in clave that. Doesn't, have rights. An authorization, to access that code right, so, here we're not talking about a software, solution. To. Encrypt, data it's a hardware based solution, right and. That. That creates like today most. Applications. That. Would run data. Or code on, the CPU, that's. When your. Security. Is at risk when. When that data is. Brought to memory and it's where people can snoop it and. That's, what the in clave is preventing, to do right so anyone, who. Will. Will not have access to that portion of. The. Access. Within the end clave could, not see anything that's happening in the end clave. We. Run this on a. Technology. From, Intel so Intel as, specific. Chips. Cool. Intel SGX. Where. We, reserved. A portion of the. Hardware a portion of the app that, brings code and data together and we build. That physical, hardware based and clave. That. Secures. Operations. Within the end clave right so think. Of this as a black box and no, one who doesn't have the key to the black box can access and see what's happening in the black box right so, your code your algorithm, runs in the black box. But. Everything that happens outside of the black box it's like it's blind to this process. This. Is just to compare a bit the different kind of hardware. That is providing, security, today right so it's very different than. TPM. Zoar HSMs. TPMS. Are usually like it's, a separate chip on the motherboard so, you have this on your laptop's today that, like if you have BitLocker on your on your laptop, that uses. The the TPM, chip set as a, hardware, based encryption, technology. HSM. So we, do HSM imager. It's like Iraqi volt for example where your store your keys on, HSM. Server. Which. Is gonna like prevent, people from accessing. These encryption. Keys on the, hardware it's again it's different than that we're. Really talking here, about an. Entity. That. Is a secure, container in which you can run your code. The. Beauty, of this the benefit of this is we, can run at this station we run at the station as a service as part of as, your confidential computing, so. All of the attestation of what's happening in the end clave is part, of being able to use the end clave in the service in Azure and. We. Also seal the end clave which, is a Microsoft, guarantees. That once, you have put. Your code and your data in the end clave then it's sealed and. Under. The conditions you specify, no one can just, reach. Through that in clave. And. If you think of this we. Offer this as a measure, as a service, but you could think also that, Microsoft. Could look at providing. This all, of these could be different. Services, right so you could decide to say Microsoft I want, you to seal and then clay for me but. I don't want to include vinegar I want that in clave to run on a specific. Location. Maybe, in a car or maybe anywhere. And. You could run also at the station as a service to say hey I like. Microsoft, at a station I have my own attestation, can I combine them together yes. But. These are modules, of how we are putting this software together. People. Always encrypted, is a great example of, how. Microsoft's. Own. Product. Are, using this ACC. Feature. Capability. Right to, to. Better and add capability, to our platform so exactly what Jacob, is going to talk about, later there today. Okay. Moving on computer I think that's the big that's, the big thing we want you to cover with you today. From. A compute perspective, we're guiding all of our hardware partners, to. Include. An ACC, an. End clave offer in, their build up right so today. We partner up with Intel, and. Most. Of the offer is built on Intel SGX, but. We're going to be partnering with other, silicon. Providers, the. Offer we're launching, in. The next few days is built, on the latest. Intel. Xeon processor. That. Has intelligence. And what's really cool is. Intel. Has made this processor. Available for Escher before it's available outside of measure so. If your user of Intel SGX today, Intel. SGX imager, is, the, latest technology, from Intel that. You, won't be able to find outside of azor for a while. This, service, is available as, a virtual, machine so. Exactly, as you consume virtual machines today from, measure, we're. Creating a new virtual. Machine. We're only DC, series and the. V DC series, VMs, are gonna have the. Configuration computing, and clave. Enabled.
They're Gonna run on this new hardware they're gonna have the ACC. Technology. Enabled. And, we're gonna it says early October actually it's as early as the 1st of October so, on the 1st of October you'll. Be able to. Go. And access these VMs. In. A. In. A public preview way right so the big difference between GA. And public, preview is, this. Is gonna be available to everyone on October 1st. We. Don't have a full-blown. SLA, yet, on. On. The under on the service right so. You'll. Be able to test it use it and. The SLA is going to come as we as we go ga with this product I. Don't. Know what do you mean by working on support we have other managed compute so let's keep on that but, that. That's the big thing right is like. Think. Of this as a V mu X is the VM and the, VM works. On on the. Intel. SGX built, hardware and you have this service accessible, as, easily. As, you access, other VM zero today. So, I'll talk a bit about the. Software-based. Portion. Of this right. When. You think of an application that is going to use a, good financial computing. Think. Of. The. Host, package, and the enclaves package, of the application, right the, host contains, the. Portion, of the application that, can run on. That. Can run untrusted, right. So you don't need necessarily to, secure. The. Portion, of that code or that application, and. What. Needs to run in the end clave is of course what is your, secret. Sauce or private, algorithm, or the data you actually you absolutely, want to make sure is in tempered right and. Building, an application for, a cc is always gonna have you consider these two things right, which. Part of the code do I need to run on the host which part of the code do I need to run in the end clave. And. It's an optimization, Taner the more code you're running the end clave, the. The, slower the execution, of that code and of. Course if you if. You and everything and the, hosted part of the applia of the. Of. The application, then it's not secure right so. Think. Of this as a. It's. Like a user. Mode kernel-mode kind. Of like dialogue between. What's. Going to be in the host where it's going to be in the end clave and how, that application needs, to be built so that, these two parties talk to each other. What. The what this means is likely the applications, you have today that you want to secure, will. Have to be refactored, to. Be able to leverage that technology, right. So if the application doesn't call specifically, for. Code. That is in the end clave and, waits, for like, in and out instructions. From. The nkf then the application, wouldn't use the technology, will use the. The. Part of ACC that makes it so secure right. So I don't want I don't want to like to oversell this I'm. Not saying it's gonna be as easy to move an application in Azure and have it benefit, from that it's, it's you, won't need to rebuild the whole application, but. The application, some parts of the application you will need to be refactored so. You understand, exactly what. Is it you really need to put in the end clave and how, do you need to call in and out data. And code outside of that in clave well into. And out of the end code. We. Are also, launching so, not on October 1st I think we're gonna launching this like October a 4/10, so. A, big, week after, the, VM is available, we're. Gonna launch or open. In clave SDK. Just. To help you build applications. And. Services. On, the. Confidential, computing, platform. I'll. Talk about I'll, talk about exactly what's in the SDK, this. SDK supports. Windows. Based operating system, Linux based operating system. We. Have. Well. If the SDK is going to be built to run until SDX but soon we'll have a, arm. Trust zone, support. As well as part of the SDK. Is. Going to be standardized, pluggable. So you, can use, ACCE, on a multi platform an. Abominable multi platform way right whether it's. It's. Gonna be Windows and Linux to start with but. It's still multi-platform. In that sense. It. Needs to going to support in, terms of runtimes gonna support C and C++, right. So we'll. Consider, and, we're working actually, on adding. Other wartime runtimes. To Confidential. In computing but. Right now the code that you're going to be using. In. The end clave that runs in the end clave needs to be in C and C++. In terms of crypto library we're, going to be using the embed TLS, later. In October so probably. Not exactly, when the SDK is gonna get out but like a couple of weeks after. Right. So this SDK is going, to let everyone using the SDK do. Include. Creation and clave management. Measurement. Of what's happening in the end clave. How, do you read and how to process the attestation.
Of, The code running in the end clave. All. The mechanical, mechanisms, to call in and out data and. What, you need to build in guiding, you and how to craft this. Application. And how. To think. And, strategize, what needs to be on the host where needs to be in the end clave. And. In. The cryptography, library as well do. I forget anything I think done. So, that's that is a repeat actually but, there yeah too close on the end clave right we, have a. Unpaved. Sorry, SDK, available October, 8, we. Are supporting. All of this linux. As an operating system, actually oliver. All of our customers, will run ACC today a good. Like 70%, of them are running Linux, code, on. Our ACC, enclaves right so well. We. Love our customers to use Windows we're totally agnostic here, in in terms, of what is, the operating system that, you. Want to run in the end clave we support both Linux and windows completely. Equally. C++. As a runtime I talked about that and. To. Day the SDK is only built for Intel SGX but. We'll have arm. The. Arm, trust own coming soon. So. In terms of scenarios I think we prepared a few demos. Hopefully. Michael can join us. But. Yeah cup do you want it you want to go over and get. Started on your sequel. Presentation. So. We had you we had you go after, Michael so, I'm gonna skip the few slides and make. Sure that we get to your slides. And. I'll give you the clicker. So. I'm, Jakob somatic I'm part from the, database. Group I work on simple, server now for sequel database, have built a bunch of security features and, currently. The. Thing. That I'm working on is called always encrypted so. Mustafa. Talked about you. Know all this work we we are doing on one side to an able you to, benefit, from from. The innovation, that T, is the, division work environments, and enclaves, provide. So. That you can build your own application. That benefit. From these technologies so that's one way you can actually consume. Confidential. Confuted computing, capabilities, the. Other trend. You're gonna see, in. Another and, the, Microsoft in general you're gonna see more, and more, microsoft. Services, and products, that use enclaves. Internally. To. Provide, the. Same benefits to you, directly. Basically. Protection. Of sensitive data, in. Use so. That's what, I'm going to talk about is, is an example, of that so, I'm going to talk about how. We. Leverage, unpleasant. Is to, bring confidential. Computing, capabilities. To. Sequel. Customers, to customers, of sequel. Server and Azure sequel, database, ok so. First let. Me first let. Me first try to map this. Concept, of, confidential. Computing, to the world, of relational. Databases, okay so. In. Database, systems. Confidential. By confidential, computing, we.
Mean A set of capabilities that. That, aim at protecting. Sensitive. Data from, high. Privileged, but. Unauthorized. Users, right and that. Means. Database. Administrators. Administrators. Of machines, hosting, your data that. Includes cloud. Admins, cloud operators. That. Includes any software, and potentially, malicious software, that can be running on a machine hosting. Your, data right so, the goal is to protect the data that. Is being used during processing. Of sequel queries. Inside. The database environment, right. So. That's the security objective, now the. Key. Other. Goal, is to achieve that first objective, in such, a way that doesn't, compromise. Database. That. Processing. Capabilities, of the database, systems, right so, what we want to achieve here, is that we want to on one side protect, the data from these, powerful. Adversaries, that I mentioned, and, on the other hand we want to ensure that. Nobody. That. That, the. Database. System that they, hobbies can continue. Reason. About the data that, can that can continue. Perform. Computations. On the data right, so, these are quite, two conflicting, goals, right and until, recently, these. Goals were mutually. Exclusive, well you could have. One but not the other, so. That's a big problem that we are trying to solve in the, sepal team how to protect. The car in use and and, also preserve, database. System sequel server engine. Capability. To, reason, about the data to perform, queries, on the data that is never exposed in plain text to, admins. Right, so. I'll. Tell you what we have done so far on this journey right towards, confidential, computing, in sequel so today, two years ago. We did the first step towards, the division by, shipping the feature called always encrypted in, sequel. Server 2016, and it's available has been available. Generally. Available in a natural sequel database, for about two years as, well so. It's. A client-side. Encryption technology. So, what this means data, is encrypted, and. Decrypted. On, the client-side, using. Keys that are never ever exposed, to. The database, system to the server side so. What this means is, that the, sequel server engine, never. Sees the data in plaintext right, and. This. Client-side, encryption also, has two other important, properties, one, is the transparency. Of cryptographic, operations, to. Your, application. So, your application doesn't, have to know what. Algorithms, are used for data encryption which, data is encrypted which isn't all, that is, figured, out automatically. By a client. Driver which, is part, of the client application such. As dub net framework a hero dub netted dubbed net framework or ODBC. Or JDBC right. So. That's that one important, property and the client driver transparently. Encrypts, anything that leaves. The client. Trust. Boundary, and is. Sent to the database, to. The database system and the and transparently, decrypt, Sanna query results, that are retrieved, from the database. Are. Encrypted, right so. That's that's one important, characteristic the. Second important, characteristic, of this current. Version of always encrypted is that. It. Provides. Basic. Confidential. Computing, capabilities. Chris mentioned that. One way to achieve confidential. Computing, is by, using homomorphic. Encryption so. This is kind of what we did in this first version we, namely, employed, what, we call deterministic. Encryption so, it's not exactly homomorphic. Encryption this. Type of encryption that belongs to the property, encryption, algorithm. Category, what, it does it always produces, the same ciphertext for, a given plaintext, value so you can call it n times and it always always give you the same ciphertext, for a given plaintext, so, what it allows us to do it allows us it. Enables, sequel server to. Conclude. That to, plaintext. Values are equal or not without, seeing them right by just comparing the ciphertext so. In. The world of relation databases, that, allows you to support, queries, like, point. Lookup searches, right or equality, joints, or simple aggregations, using group by operations, right so, you can do that in, a confidential, way and that's what we did in this first version, of always encrypted. But. Of course, equality. Comparison, is not sufficient, for many applications if. You have an application that processes. A broad, set of personally. Identifiable, information, such. As names addresses, phone numbers and so on right you, you likely need more than just equality, comparison, you would like to do. Pattern. Matching or, sorting. Or or maybe, automatic. Operations. Or on some, numerical, sensitive. Data right so, that is not possible when, the current version that is publicly. Or has been generally available for quite some time. The. Other problem, that exists. Today that customers. Using this this, current version of always encrypted have, is well. Sequel. Server doesn't. Have access to the keys that kind of the principle, of of our current, design right so, that means that sequel, server cannot, perform any cryptographic, operations, on.
The Data ID all right which, means that if you need to encrypt, your data for, the first time or if you need to re-encrypt, it the writer later on to rotate encryption, keys right, you. Need to move all the data outside, of the database perform. This desired cryptographic, operation. Outside of the database and upload your data back right so, you can imagine that doesn't. Scale very well and it's prone to network errors and also it, causes all kinds of security and compliance problems. Because now this place that you're moving the data to, it needs to be a part of your compliance, boundary, and so on and so on right so not a great story so. We. Are going to solve these two problems by. Leveraging T's, or on plates Christophe, talked about right so. The way we're gonna do that it we basically, we. Morph sequel, server into. An enclave. Application. So. Sequel. Server now. Can. When. It starts, it will initialize. An enclave it will contain, an enclave right in, this unplayed. Will. Act as an extension, of the client-side. Trust. Boundary, right so, you, know and always encrypted kind. Of a thread model the. Client, is trusted, and sequel server is on trust right that's the that's, the assumption, so now on the server side we have this unclaimed, they that. Acts as a as an extension, of the client, it's like. Agent. Behind enemy, lines right, or like. And. Foreign, office an embassy in a country, right. So. The, way we're gonna use this on play server. Will basically, delegate. Certain. Computations. On the data to. The Enclave, right and remember the data is stored in he encrypted, form and that's what sequel, server the untrusted, part of it at least can access so. Now it will send this encrypted, data to the Enclave, and the, Enclave being. The execution, environment, right it. Can now safely decrypt. The data and. Having. Access to plain text it, can do whatever it wants right sky, is the limit it can perform in. General, arbitrary. Computations. On the data having, access to plain text however, we are starting, with what, our customers, ask. Most. Frequently for. Pattern. Matching range. Queries, this kind of things right and. Also we, want to enable what we call in-place encryptions so now having. This trusted. Entity on, the server side we, can leverage that fact also to, support. A. Cryptographic. Operations, without. Moving, data outside of the database right so. You. Get this. The. Feature will become more. Useful and more scalable. Especially. In, conjunction, with large, data sets right so. Let. Me actually show you how this works. Using. A simple demo. Let. Me make sure we are connected, here. All. Right you can see it's perfect, so.
For. My demo I'm. Going to use a, very, simple database. House, it has just one table, and, this, table contains some, fairly sensitive, information at, least in two columns so we have as, a sine column which, for. Non-us. Participants. These are government. National, IDs that. We use in the US and it. Stores some salaries. Of employees right. So. That's that's. The database side, and now I'm. Wearing a heart of a DBA right I just ran this query I can see all the data with, no problem, right and, if I'm an, admin on this machine I have, even more techniques. To get, to this data right I could, do the memory scan, of the sequel server process. I could, generate a dump file and find all that information there in plain text right so. That's. That's the problem we, want to solve before. We do that though I want to show you another part. Of the demo, I have this very simple sample application. That. Basically, displays, all this employee information and. The one little detail that I want. To show you here, is, I have these filtering capabilities. Right so I can filter, these employees. By salary, and I can filter them by a portion of the social security number so, nothing nothing, special. But. I want to also. Call. Out one important, thing whenever I use, this UI this application, triggers, a query. A sequel, query against. The database so, I want to show you how the score looks like. Okay. Let me see if I can open it, all, right. So. As. You can see this is a fairly. Simple, query, but at the same time it. Performs. A fairly rich operations. It. Contains, a pattern, matching operation, that's the like predicate, right on the SSN, column it contains, the range comparison. On the salary column right so, it performs, these rich computations. To filter, the result set so. What we want to do in this demo we, want to do two things we want to protect that, sensitive data and SSN and salary columns, from high, privilege but unauthorized, users we, don't want the DBA to be able to see that data in plain text that's one goal but, also we, want to we. Want to make sure that this application can, continue. Issue. This rich, rich queries in, the unchanged, way so we don't want to change the application we want these queries, this particular, query to remain, as is, and continue, to work right, despite. The fact that sequel. Server, will. Have the data encrypted, so let's let's, do that. So. Normally. The first step in configuring always. Encrypted you need to provision some keys I'm skipping that because that's not so interesting so, I have, pre provisioned. Some, cryptographic, keys. Before. The demo so, now I'm going to use them and I'm going to encrypt, these two sensitive, data columns, and. With this version of always encrypted using enclaves, it's a very simple operation that, you can issue. Using, using, sequel, and completes. It instantly. Well in completes, instantly, for two reasons first I have a very small, data set but they're more important, for, this discussion reason. Is the fact that this operation happens, locally in place in, the, local arm clade on the server side so, that's one thing now so our data is already encrypted, at this point let. Me now do, the following I will rerun, this query so what you see are the results, of the previous run before, encryption. I'm, going to rerun it and, I now you can see that if I'm a DBA right if, I'm an admin I count the memory of the sequel server process, this, is what I'm gonna get I'm gonna get some, encrypting, blobs for SSN, and some, encrypted, values for salary right, so. We. Protecting. Sensitive, data in news now now, let's see what. Kind of impact if any it, had, on our application okay, so. I will move to our application.
Let Me actually refresh, it so. This. Still works so, the, reason this. Part works is that, the. Client, drivers are I explained to you earlier it, gets, encrypted. Results. From. From. The database, but, then it transforms, it decrypts the results, and returned, plaintext, to the application, the application as. I mentioned earlier is trusted, it has been configured to have access to these cryptographic keys, are used, to encrypt these two columns right so. So, that's one thing and this, part was possible, it's possible even with the current version of always encrypted now, the new. Cool thing is that. These. Filtering, capabilities. To work so. I can filter these employees, by salary. Range and by, social security number despite, the fact that these columns as you saw, are encrypted. Right so. Now let's. See if queries. That the application, sent to the database changed. In any way okay so. Let's, use. This monitoring. To all that leverages, extended, events and let. Me see if I can. Open. This. So. There. Are two things to note here so. First of all the query statement, is identical. As before it has not changed we. And it works still. As you saw because the application, was able to filter right the, second thing to notice that now, the, search, criteria the, parameters, of these queries are sent. To sequel, server and he encrypted, form so they get transferred he encrypted. On the driver side the. Server gets them encrypted, right so, the server has encrypted. Parameters, encrypted, data in these two columns what, it does now is that. You don't see here it. Sends, the data to D Enclave D Enclave say if we decrypt, the, parameters, and that the, data and performs. Execute. These, predicates. Contained, in the query like and range comparisons. Right so, what I achieved here I protect. Sensitive data in use a while. Preserving, query, processing, capabilities. Of the databases, so. By the way this is something that you can try today earlier, this morning we announced, that public leave your sequel, server. On-premises. Which uses VB as Enclave so actually different technology, that would what do we use in after however, you're, gonna see the same in our other, sequel, database, in particular, we. Are in the process of. Developing. And migrating, this, implementation, to Intel SGX and, and. So that you can take advantage of it in our as, well if you want to learn more about this fascinating technology. Join, me this Thursday, I have a session. Entirely, dedicated. To, this topic, Thursday. 10:45. Confidential. Computing, and sequel using, secure enclaves with, that I'll hand over talk, to you crystal Thanks. Just. Switch back to oh yeah. So. We have one challenge as my second. D more as not arrived yet so, apologize. To everyone for that I. Could. Give it a try and talk to you but blockchain. But I'm not really the expert so I wouldn't, be doing you a huge favor. Maybe. At this point what I propose is we, take your questions, Jacob and I write. Because, it's. A topic where we can go pretty deep and if you guys have questions I know, everyone some some of you are like experts, in there and you probably want to know more than what we covered some. Of you feel like overwhelmed, already with all the. Content so let's.
Do This let's go through a QA. And hopefully Michael will show up if, he, does not, then. We'll close them. Any. Questions for yes, please. This. Is a question about sequel, part or general. Question about our. Shore confidential, computing. As. Well, get. Started with people yeah so. Let. Me make sure I understood and I remember, the question correctly so the. Question is how. Do we transport, how do we send the keys to the Enclave and how can we make the arm play. Capable. Of decrypting. The data is that the question. Okay. Where the keys are stored. Right. And okay. Sounds. Good so. The. Question is what do we store and how do we manage the keys, and always encrypted so, with. Or without enclaves, keys, are never ever stored, ins on, the sequel server side that's one thing to remember now. In sequel. Always. Encrypted we have two types of keys we have symmetric. Keys that are used to encrypt data and, we have our symmetric keys key protectors, right we call them master keys so, these symmetric keys are stored, in sequel server but always in, the encrypted form so I meant to say earlier was that we never store them in plaintext and sequel so they are starting he encrypted, form in sequel, a symmetric. Keys however, the master key so-called can be stored anywhere you, want. We. Out of the box provides support for storing, them in our keyboard, in HSMs as you mentioned in the windows certificate. Store right now, with, enclaves, key management meant, not, maybe not key management but key usage scenarios, become a little bit more complicated so one. Thing I told you earlier was, that sequel. Server doesn't have these keys and plain text but on the other hand I told you that the Enclave needs to decrypt, and encrypt, and re encrypt the data and, the, Enclave, is part of the sequel so how does the Enclave get the keys right so, the answer to that is that before, the first use of the Enclave the client, application that, has, the access to the keys creates, a secure, connection a secure tunnel an equivalent, of SSL, connection, to the Enclave through the untrusted, sequel server and hydrates. The Enclave with the right keys needed to for, query processing. So, that that's, the part of about, sequel, I don't, know what we can tell, in general about key management in. ACC. You. Yes. So thank you Christopher, and my name is Michael Glaros I'm a senior. Product. Manager in the Azure blockchain engineering, team and, we've, been very closely, partnering, and working with the confidential, compute team because. We we hear this business problem very frequently, from a lot of our blockchain customers, around. This idea that without, confidential, compute without the use of enclaves, there, are some very pragmatic. Challenges, that are really blocking much. More widespread adoption of, blockchain technology, especially. In scenarios, with a high degree of regulatory requirements. Or or security, requirements, or, at scale so, if we just take your, average aetherium, ledger or kurta, or hyper ledger fabric node and you run it in a docker or in a VM SKU today, you're. Gonna see these three fundamental challenges. One is scalability. Because, watching systems, by their very design it's it's a computationally. Intensive, exercise, to. Actually achieve consensus, across the network so, one problem is you have the physics, associated, with round-tripping. Across the network these are peer-to-peer nodes they, have to achieve consensus, with one another so we need to make sure that all. Agree, before the before the block is committed. This. Combined, with the computation, that's going on on the node itself can, really add a lot of friction, and latency to the to the processing, and the transaction, times, second.
Is This idea of confidentiality, well, by its design most, blockchain, smart contract, systems, will, write the data in clear and share, that across the network so any participant, in the network whether, it's a public network or even a permission network, they, would have access by default to the full contents, of the ledger so if, you have scenarios, where you want a certain degree of openness, across the community, however you still have requirements, for point-to-point, encrypted. Meshes payloads this, becomes very difficult to manage and typically, what we see is customers, have to incur lots. Of expense lots of complex, in terms of key management and crypto, and there's some novel, very, complex, things like zero knowledge proof sand, homomorphic, encryption that's, kind. Of making its way through but, it's very difficult it's very challenging, and complex to implement and then, finally the idea of governance so. If I have if, I have these counterparties, that are coming in they're just standing, up these blockchain, nodes and connecting them, what's. What's the SLA, what's the commitment, between the counterparties. What. If somebody is behaving, maliciously, in trying to game the system can I kick them off the network these, things become programmatically. Very difficult, to achieve if, I don't have some framework, that that's ties it together so, what. We're able to do taking advantage, of confidential. Compute is this, idea of the confidential, consortium, block team framework, previously. You might have heard of cocoa framework this is kind of now the the, more official name. If you will going to market the, idea is we have this open-source, framework that. Through, an architecture, we're going to look at here momentarily will allow all of these counterparties. To come together and, achieve, much, greater transactional. Throughput, much. More reliable, security by virtue of the fact that we'll have key. Management structures, and certificate, identification. Structures that will go out to each of these nodes each of these participants, so. Then the idea being if I'm a new participant, coming into the network there, are some cryptographic, primitives. I'm going to be expected, to contribute to, the CCDF, to authenticate, and authorize my node before it'll start trading on the network and, then finally, the idea then of these, enclaves, supporting. A wider array of consensus, mechanisms, so, I'm no longer bound to just say proof-of-work. Or the. Standard, default but you know Byzantine fault tolerance consensus. Mechanisms, that the ledgers impose upon me instead. I can do more of a standards, you know Paxos based or or much, more highly, scalable, familiarized. Distributed. Computational. Algorithm. To get that consensus, across the network so, architectural, II speaking again, it's based on the core principles that you saw earlier about, the. The Enclave and. A confidential. Compute basically, we have on. The left there your, you, can have your administrator. You can have your distributed. Applications, your, smart, contract applications, the, idea is that these process, through this CCDF interface, that, sits on the validating, node that, then interacts, with this Enclave you know so you imagine this is your perhaps. Through your SDK. SGX. SDK for smart, contract, that. Then sits in front of three, distinct structures, you have your your, state of affairs relative, to the consortium relative, to the network you, have your blockchain, core and so what we envision is this will be the blockchain protocol, of your choice so if you want to run etherium here you want to run hyper ledger fabric, or kurta with. The adapter that then syncs it into the larger, CC bf and then, finally, to give us that hyper scale throughput. You're, gonna have this replicated, persistent, store so you'll have a a. Typical. Familiar. Sequel. No sequel type structure, there at the back-end to cache these transactions, to expedite, the throughput and really, give you kind of that hyper scale performance, experience, for, those workloads, that you know maybe would, otherwise adopt blockchain, were not for the, long processing, times associated with achieving consensus. So. If we look at aetherium specifically. For the moment, what. We envision, is that using. The enclaves, we're, going to have this ability to put the ledger and the smart contract execution. In. An appropriate, access control model so the idea is make. Things available via, API, and, smart contract, that are okay to run in the clear yet, when we get into the actual data itself that might only be authorized.
For Certain counterparties, in the trading network those, things should live in the Enclave, where, in order to access that information you're, gonna be challenged for keys and you're gonna have to be able to present your nodes keys to, be able to see and reveal that data you. Can actually, disable. Access at the, block level so, again is you, think of a ball chain it's the sequence of transactions, that's happening, and right. Now it's kind of an all-or-nothing deal typically, where you've got the entire sequence being shared across the network and as each network, copies, that transactional. Ledger you're. Gonna have access to the thing well what this framework allows is maybe certain blocks in there are redacted from certain counterparties, so you might imagine that, you'll. See a sequence of transactions, that are available for the whole network yet, then a block of ciphertext, for only those parties, who. Are not authorized, to be able to reveal the transaction, and, then finally, having this verification, of the, caller because again block teen is fundamentally, a peer-to-peer network so. I need to be able to authenticate and authorize who. It was that actually invoked, the smart contract so. Today again it's basically an all-or-nothing, deal anybody, who's on that network again whether it's permission or private is able, to as long as they know the address of the smart contract they call it they place the transaction, everybody gets a result once consensus completes with, the CCDF the, idea now is every. Node is authenticating. And authorizing per. Transaction, so. Now before the node attempts. To use a transaction, I can, interrogate that node I can confirm, they're authenticated and authorized to perform that operation and, then, simultaneously I, can follow that through to to the data payload level, as well. So. That's. All we have there from from. The CCDF, perspective. Question. Questions will be great anybody, have any questions on. Well. I mean just purely, on blockchain, there's. Not necessarily a limitation, other than the. Amount of storage. Key you. Know storage allocation you've, set aside I mean it's elastic so you're gonna you, know so there's not necessarily a limitation, other than just continuing. To grow at scale from. From enclaves, and from te. It. Was unwritten 28. I. Think. It's I. May. Be wrong cos like because. We're releasing the, the. In a few days I know like we. Might have like, improved the service in the last few minutes but like having was under 20 inmates so, fairly small right that's why it was mentioning he, needs to be a conscious effort. And. Also to there's some some reference material up, here as well that you can certainly. Photograph. And take, with and, research. As well right. But he needs to be that the conscious, effort of like what is it you're gonna put in the end clave what, is it you're gonna put outside of the anklet right because the enclaves is fairly small so. You cannot you cannot put everything in there right so, as. You approach the. Application, building means really think like this. Piece of data this piece of code needs to be in the end clave this, can't, afford not to be in the end right and and today, that is the the challenge, of building for ACC is how. Do you strategize, for that. Go. In the back first. Well. I think that is, with with anything again clearly, from the block team perspective and then and in Te King can comment I think it starts with good risk, fundamentals, right so I think that right now. You, know a lot of the primitives we've seen around sort, of the SGX SDK, is you'll. See. Better. Access, restrictions, and and and and flow, control integrity. Strut. Control structures around the Enclave, itself but, maybe not so much the SDK so I think the trick is is you have to like risk assess each. Step along the way and each input and output into, it, and. Really. You, know test prove, experiments. Before. You kind of go, any. Further for, you, know a spectrum style attack I don't know yeah, no so like we. Learn a lot from these kind of events right and I think it's, it's it's it's a.
Virtuous. Cycle of like learning and, fixing. And they're running and fixing right I think no system is ever like. Proof. Like totally. A tholian temporal, right. But. With ACC when the data is encrypted in, storage. In transit, any news, it. Gets really hard right I mean like if you think if you think about this it gets it gets really really hard to. Try attack. Data or, get access to data and even you could get access to data it's encrypted right, so, I. Don't. Have specific, comments about these two events right but I think, this. Is happening this is gonna happen again right but, the, whole industry, is, improving. And really, limiting, the window of like. What. What is it did you could do next to go to go, and attack a system right. You. Know we had another yes sir. I think. So right I wouldn't see why not I mean basically if you if you're deploying the SKU that has the X Y X enabled. And. Then you just deploy the container on top of that SKU I mean, as long as you're as long as whatever code you're running is running within that Enclave it should, be able to now, in terms of that's, bound to have interfaces, on the, registry. Or the control plane for that that container you may have some additional authentication. And authorization work, to do. But. Theoretically. It should at least work and it should definitely offer an, improvement to security. Right. So there is a question about when. The always, encrypted technology, with on trees are described, - which are the flavors of azure sequel, database, or. Sequel. In Azure in general that's gonna be supported, and so, first of all I want to repeat. And emphasize at, this point that publicly. What is available today is, not another, as. Of today you can, use sequel, server and install it in your own Prem environment, however we, are on path to enable it another and, our goal. Is to make sure that this feature is available in, all the flavors, of sequel, another including. Elastic. Poles likely, and and a. Sequel. In a VM I don't, have a specific timeline, for that but that what we gonna work on very hard after, we, very. Close to completing this work in sequel server romper. Yeah. I was like yeah. Sure. So there was a question how, about protecting, the data on the on, the client-side or I guess we could expand. Your question, and ask you.
Know If we envision, an application, to be a distributed. Application that, uses different, services, in order perhaps, like. Some of it may be in hosted, in other. Websites. There. Are web components, that you hosting another. Why. Don't. Protect that data as well I mean. That that's the Nirvana. Kind of idea of vision we we. Heading, towards. We. Are, doing some effort in. That direction, with. Multi-party. Machine. Learning. Which. Which is which kind, of solve similar problems. So. Yeah that that could be the next logical step we don't have a timeline for that yet but again. There. Is no technical reason why that should, not be possible in. The blockchain world you're starting to see this idea of like hardware wallets gaining, a little bit of traction and this is marriage between you know the client you know if we think of the wallet is the client class client, application, and then, being able to actually use, that as the basis to transact, with you, know the web distributed app or even the ledger directly, so, I think it's coming I think it's just early, days and I think that, developments. Like confidential, compute like having, readily. Available, VM. Skews with with the Enclave technology, accessible, for experimentation, and, prototyping. And further development is only going to expedite and get us closer to the, client side on, claiming I think, that that's that's my, point the closing word right it's it's very early. We're. Just releasing this our hardware. Partners they're just working on improving the technology every day someone. Had a question about the size and I was like struggling to answer because that changes. Almost daily right. We're. Very excited with the launch of the SDK, because that gets this technology, in the hands of like millions. Of develop, right, that can come with very smart ideas like you're just you had right and and will. Will build over time what's the co system for confidential. Computing, but. If you think about this if, you have that data encrypted in transit in, storage any news, that's, sort of like the holy grail of, how. We make the cloud super secure for everyone to use and, everyone. To use what whatever they need to use the Klat for and now to have this. Struggle, of like, that. That thing is my is my key data it's my key code can i really trust the cloud with, this right, and that's that's, the barrier we're, trying to breach is that. Developers. And, companies can bring, data. And code to the cloud you fool trust. And. I think we're in the early days of that but that is gonna change the way people consume clad we think and why, world's super excited with this, and. You have to leave again either the guy is a rock star it's like yes. Like one session every ten minutes thank you Michael. So. We're, real close here I think we don't have any more slides the next one is if. You want to take a picture of this one it is some like interesting, links. Nothing's. Better, than like taking, a picture of the link and go, back and typing the link and a brother, but, that's secure. Yeah. That was a last slide so thank, you what we'll take questions as, you, have them cuz I saw, a few hands that we're. Raised and didn't get an opportunity answer your questions I. Don't. See any more well. Thank you all thank you for your, time the last less, cloud of the of the day thanks. You.
2018-10-13 19:07


